Hi everyone!
I am trying to get my mail server set up … but I cannot send or receive e-mails. Also, please note that I haven’t yet got an SSL certificate for the subdomain mail.mydomain.tlp.
Here is what I have done thus far …
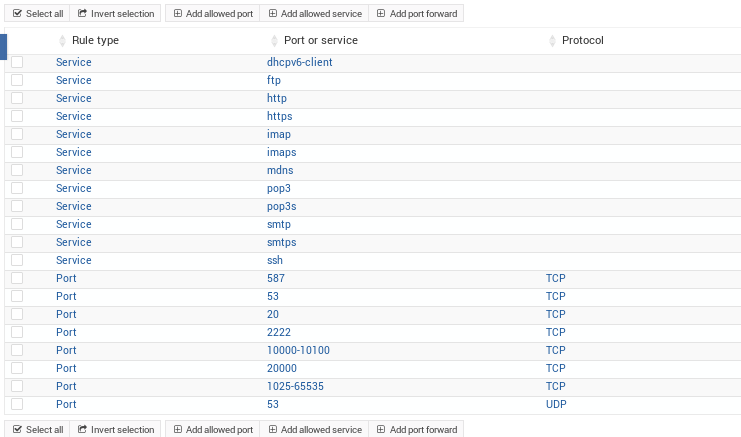
- a) opened ports 25, 143, 587 and 993
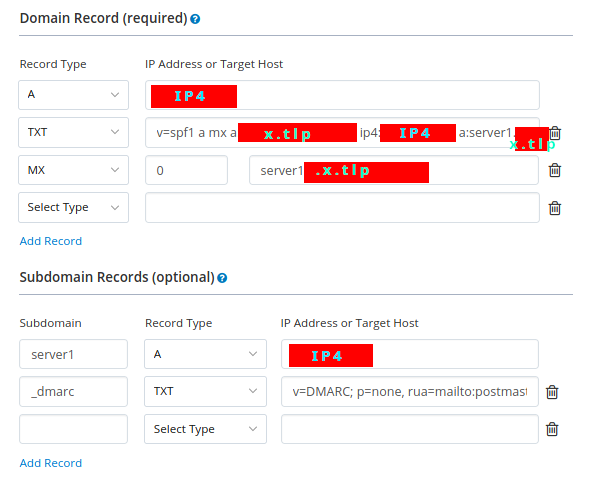
- a) created an MX record on my registrar pointing to mydomain.tlp
- a) created a Mail user
- a1) logged into Thunderbird - bypassed the warning
- a2) VMin > Email Settings > Mail Cli. Config > Cli. Autoconf. > Yes
- a2) logged into Thunderbird - bypassed the warning - deleted the “mail” subdomain so it IMAP points to “mydomain.tlp”
- a3) copy LE SSL certificates for mydomain.tlp and www.mydomain.tlp to Postfix and Dovecot
- a3) VMin > Email Settings > Mail Cli. Config > Cli. Autoconf. > Yes
- a3) logged into Thunderbird - bypassed the warning - deleted the “mail” subdomain so it IMAP points to “mydomain.tlp”
- a4) copy LE SSL certificates for mydomain.tlp and www.mydomain.tlp to Postfix and Dovecot
- a4) log into Thunderbird
Path a1 defaluts to port 143 for IMAP and no idea what port it uses for SMTP, but it issues a warning.
Path a2 defaults to port 993 for IMAP and 587 for SMTP, but it issues a warning that there is no encryption.
Path a4 is what gives me the best feeling thus far, but mail is not being sent or received …
Troubleshooting
host -t mx mydomain.tlp
points to mail.mydomain.tlp
host mail.mydomain.tlp
EDIT: points to my IP address
whois mydomain.tlp
shows my name servers (glue records?) are my registrar’s
Any ideas on how to proceed? I am quite lost.
Thanks in advance ![]()


 I am giving it up for now. There is no way on Earth my landlords are giving me access to their ISP’s account … I will try again when I move to a new apartment in the distant future. Thanks for the support guys. It has been interesting =)
I am giving it up for now. There is no way on Earth my landlords are giving me access to their ISP’s account … I will try again when I move to a new apartment in the distant future. Thanks for the support guys. It has been interesting =)