Shinzan
January 18, 2021, 11:20pm
1
UNUNTU: 18LTS:
I have a virtualmin server that runs web and mail on 192.168.0.8 and I use portforwarding for web and mail as it sits behind our corporate firewall.
Well postfix is running port 587 TLS but im getting blocked by all these ridiculous appliances like baracuda and others and they tell me you “dont support TLS” well obviously I do, its just running on port 587 not 25.
Is there a work around for this or do I have to run postfix and my entire box on a Public IP instead of NAT?
587 is the submission port. 25 is the relay port.
Why not just forward both ports in the firewall to their respective ports on the server?
Richard
I have forwarded both ports but the TLS check fails on tools such as MXToolbox
If I telnet to 25 it shows StartTLS isn’t an option anyway where can I enable it?
EHLO Test.com
250-virtualmin.myserver.com
250-SIZE 31457280
250-VRFY
250-AUTH PLAIN LOGIN
250 DSN
Joe
January 19, 2021, 1:10am
4
I think it should be automatic as long as you give it a certificate.
Something is definitely not automatic, I have a godaddy Turbo SSL (wildcard cert) for www. tld.com mail.
and the sub domain shows my cert and the parent domain shows the cert but I can’t get a website like
to show me as “secure”
now I have another virtualmin box running on a public IP no NAT Firewall and this problem doesn’t exist, I think part of the issue is at least that STARTTLS is a command that is not available over port 25 of telnet on a mail session, whereas on port 587 it is
I also know the port forward for 25 works because can verify via telnet from an external network. So there is something I have to enable that has either been disabled by accident or something that is broken since
telnet myserver.com 25
doesn’t give me the starttls command
Is there any paid service for Virtualmin anyone would recommend for a troubleshoot, I know they have that portion closed down now on their site. I just need it to work and dont have a ton of time to track it down but any help is much appretiated
Have you copied the SSL cert to Postfix?
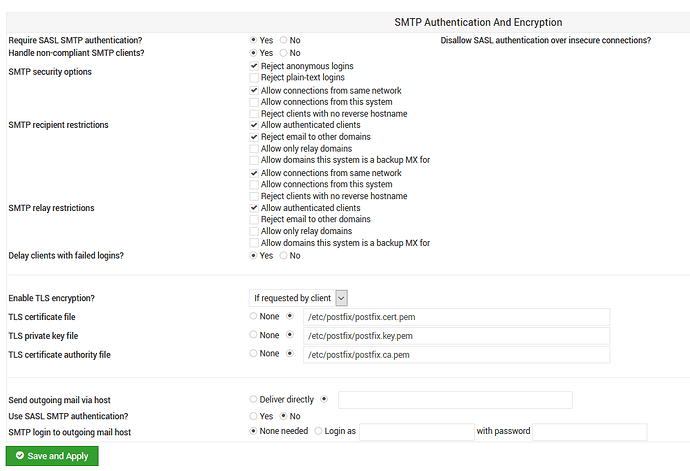
Have you checked that the cert paths are correct in Webmin > Servers > Postfix Mail Server > SMTP Authentication and Encryption?
On that same page, have you enabled TLS encryption in the section aptly titled “Enable TLS Encryption?”
Those are good places to start.
(If you’re using SNI, there are some other things to check.)
Richard
yes on copy to postfix, I just pressed the button on virtualmin domain to copy the ssl to everything, on the page it reads:
This SSL certificate is already being used by : Webmin (tld.com ), Webmin, Usermin (host tld.com ), Usermin, Dovecot, Postfix, ProFTPD
for enable TLS encryption? it is set to “if requested by client”
Shinzan
January 19, 2021, 1:53am
10
I even did a sanity check on the copied key in postfix vs the one in apache
root@mail:/etc/postfix# nano /etc/postfix/postfix.key.pem
and they are identical to the ones being used on the Manage SSL certificates portion of Virtualmin
What do you have selected for Disallow SASL authentication over insecure connections? Although Postfix is not my forte, I’m pretty sure that needs to be “No”.
Richard
I think @calport may be the one you need to help you with this. He’s forgotten more than I know about Postfix.
Richard
Joe
January 19, 2021, 2:55am
14
Post your master.cf and main.cf.
Edit: you can strip comments to make it more compact.
Shinzan
January 19, 2021, 3:00am
15
master
smtps inet n - - - - smtpd -o syslog_name=postfix/smtps -o smtpd_tls_wrappermode=yes -o smtpd_sasl_auth_enable=yes -o smtpd_reject_unlisted_recipient=no -o smtpd_client_restrictions=$mua_client_restrictions -o smtpd_helo_restrictions=$mua_helo_restrictions -o smtpd_sender_restrictions=$mua_sender_restrictions -o smtpd_recipient_restrictions= -o smtpd_relay_restrictions=permit_sasl_authenticated,reject -o milter_macro_daemon_name=ORIGINATING
#628 inet n - - - - qmqpd
smtp inet n - y - - smtpd
-o smtpd_sasl_auth_enable=yes
pickup unix n - y 60 1 pickup
cleanup unix n - y - 0 cleanup
qmgr unix n - n 300 1 qmgr
#qmgr unix n - n 300 1 oqmgr
tlsmgr unix - - y 1000? 1 tlsmgr
rewrite unix - - y - - trivial-rewrite
bounce unix - - y - 0 bounce
defer unix - - y - 0 bounce
trace unix - - y - 0 bounce
verify unix - - y - 1 verify
flush unix n - y 1000? 0 flush
proxymap unix - - n - - proxymap
proxywrite unix - - n - 1 proxymap
smtp unix - - y - - smtp
# -o smtp_helo_timeout=5 -o smtp_connect_timeout=5
relay unix - - y - - smtp
showq unix n - y - - showq
error unix - - y - - error
retry unix - - y - - error
discard unix - - y - - discard
local unix - n n - - local
virtual unix - n n - - virtual
lmtp unix - - y - - lmtp
anvil unix - - y - 1 anvil
#
# ====================================================================
# Interfaces to non-Postfix software. Be sure to examine the manual
# pages of the non-Postfix software to find out what options it wants.
#
# Many of the following services use the Postfix pipe(8) delivery
# agent. See the pipe(8) man page for information about ${recipient}
# and other message envelope options.
# ====================================================================
#
# maildrop. See the Postfix MAILDROP_README file for details.
# Also specify in main.cf: maildrop_destination_recipient_limit=1
#
scache unix - - y - 1 scache
maildrop unix - n n - - pipe
flags=DRhu user=vmail argv=/usr/bin/maildrop -d ${recipient}
#
# ====================================================================
#
# Recent Cyrus versions can use the existing "lmtp" master.cf entry.
#
# Specify in cyrus.conf:
# lmtp cmd="lmtpd -a" listen="localhost:lmtp" proto=tcp4
#
# Specify in main.cf one or more of the following:
# mailbox_transport = lmtp:inet:localhost
# virtual_transport = lmtp:inet:localhost
#
# ====================================================================
#
# Cyrus 2.1.5 (Amos Gouaux)
# Also specify in main.cf: cyrus_destination_recipient_limit=1
#
#cyrus unix - n n - - pipe
# user=cyrus argv=/cyrus/bin/deliver -e -r ${sender} -m ${extension} ${user}
#
# ====================================================================
# Old example of delivery via Cyrus.
#
#old-cyrus unix - n n - - pipe
# flags=R user=cyrus argv=/cyrus/bin/deliver -e -m ${extension} ${user}
#
# ====================================================================
#
# See the Postfix UUCP_README file for configuration details.
#
uucp unix - n n - - pipe
flags=Fqhu user=uucp argv=uux -r -n -z -a$sender - $nexthop!rmail ($recipient)
#
# Other external delivery methods.
#
ifmail unix - n n - - pipe
flags=F user=ftn argv=/usr/lib/ifmail/ifmail -r $nexthop ($recipient)
bsmtp unix - n n - - pipe
flags=Fq. user=bsmtp argv=/usr/lib/bsmtp/bsmtp -t$nexthop -f$sender $recipient
scalemail-backend unix - n n - 2 pipe
flags=R user=scalemail argv=/usr/lib/scalemail/bin/scalemail-store ${nexthop} ${user} ${extension}
mailman unix - n n - - pipe
flags=FR user=list argv=/usr/lib/mailman/bin/postfix-to-mailman.py
${nexthop} ${user}
submission inet n - y - - smtpd
-o smtpd_sasl_auth_enable=yes
main
uucp unix - n n - - pipe
flags=Fqhu user=uucp argv=uux -r -n -z -a$sender - $nexthop!rmail ($recipient)
#
# Other external delivery methods.
#
ifmail unix - n n - - pipe
flags=F user=ftn argv=/usr/lib/ifmail/ifmail -r $nexthop ($recipient)
bsmtp unix - n n - - pipe
flags=Fq. user=bsmtp argv=/usr/lib/bsmtp/bsmtp -t$nexthop -f$sender $recipient
scalemail-backend unix - n n - 2 pipe
flags=R user=scalemail argv=/usr/lib/scalemail/bin/scalemail-store ${nexthop} ${user} ${extension}
mailman unix - n n - - pipe
flags=FR user=list argv=/usr/lib/mailman/bin/postfix-to-mailman.py
${nexthop} ${user}
submission inet n - y - - smtpd
-o smtpd_sasl_auth_enable=yes
inet n - n - - smtpd
-o syslog_name=postfix/smtps
-o smtpd_tls_wrappermode=yes
-o smtpd_sasl_auth_enable=yes
-o smtpd_client_restrictions=permit_sasl_authenticated,reject
-o content_filter=smtp-amavis:[127.0.0.1]:10026
root@mail:/etc/postfix# ^C
root@mail:/etc/postfix# cat main.cf
# See /usr/share/postfix/main.cf.dist for a commented, more complete version
# Debian specific: Specifying a file name will cause the first
# line of that file to be used as the name. The Debian default
# is /etc/mailname.
#myorigin = /etc/mailname
smtpd_banner = $myhostname ESMTP $mail_name (Ubuntu)
biff = no
# appending .domain is the MUA's job.
append_dot_mydomain = no
# Uncomment the next line to generate "delayed mail" warnings
#delay_warning_time = 4h
readme_directory = no
# TLS parameters
smtpd_tls_cert_file = /etc/postfix/postfix.cert.pem
smtpd_tls_key_file = /etc/postfix/postfix.key.pem
smtpd_use_tls=yes
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
# See /usr/share/doc/postfix/TLS_README.gz in the postfix-doc package for
# information on enabling SSL in the smtp client.
smtpd_relay_restrictions = permit_mynetworks permit_sasl_authenticated defer_unauth_destination
myhostname = virtualmin.jancare.com
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
myorigin = /etc/mailname
mydestination = mail.jancare.com
relayhost =
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
mailbox_command = /usr/bin/procmail-wrapper -o -a $DOMAIN -d $LOGNAME
mailbox_size_limit = 0
recipient_delimiter = +
inet_interfaces = all
inet_protocols = all
virtual_alias_maps = hash:/etc/postfix/virtual
sender_bcc_maps = hash:/etc/postfix/bcc
home_mailbox = Maildir/
smtpd_sasl_auth_enable = yes
smtpd_sasl_security_options = noanonymous
broken_sasl_auth_clients = yes
smtpd_recipient_restrictions = permit_mynetworks permit_sasl_authenticated reject_unauth_destination
allow_percent_hack = no
message_size_limit = 31457280
mime_header_checks = regexp:/etc/postfix/mime_header_checks
milter_default_action = accept
milter_protocol = 2
smtpd_milters = inet:localhost:8891
non_smtpd_milters = inet:localhost:8891
smtpd_tls_security_level = may
smtp_tls_security_level = dane
default_destination_concurrency_limit = 40
#Added 8/19/2020 known spammer list
smtpd_sender_restrictions = check_sender_access hash:/etc/postfix/sender-reject
smtpd_tls_CAfile = /etc/postfix/postfix.ca.pem
smtp_use_tls = yes
Joe
January 19, 2021, 6:37am
16
All of that looks right to me, and the relevant stuff matches what we have on our servers that do offer STARTTLS. Are there errors in the maillog when restarting the postfix service?
Are you up to date? Maybe there’s a bug in postfix (though I don’t think I’ve heard of any bugs in this area, and it seems unlikely).
Have you restarted Postfix since giving it a cert and insuring it has the right smtpd_* options? (Since you’re gonna restart and watch the log for errors, that’ll kill two birds with one stone.)
Joe
January 19, 2021, 6:43am
17
And, to be clear, this is what should turn STARTTLS on or off for smtpd.
And, that’s the default in a Virtualmin installation.
See here for full Postfix docs on it: Postfix TLS Support
Joe
January 19, 2021, 6:51am
18
So, um…dumb question, but are you absolutely sure you’re connecting to your Virtualmin server? i.e. is DNS right (or are you hitting it with the IP address)? Even without STARTTLS working, your SMTP conversation over telnet above looks like it’s missing a bunch of stuff that a Virtualmin+Postfix system would say. Makes me think you’re talking to some other server or a weird proxy at your ISP or something.
Joe
January 19, 2021, 6:52am
19
This is one of our systems:
$ telnet virtualmin.com 25
Trying 198.154.100.99...
Connected to virtualmin.com.
Escape character is '^]'.
220 new.cloud.virtualmin.com ESMTP Postfix
EHLO test.com
250-new.cloud.virtualmin.com
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-STARTTLS
250-AUTH PLAIN LOGIN
250-AUTH=PLAIN LOGIN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
421 4.4.2 new.cloud.virtualmin.com
Notice that in addition to STARTTLS we’re offering an AUTH compatibility thing, and others. I don’t run Ubuntu for any real systems, so I can’t test there, but…seems like it’d be similar.
Took a quick look on my newest Virtualmin instance with Ubuntu:
root@sf1:~# telnet alpha.domain.no 25
Trying 2a0f:9xxxx
Connected to alpha.domain.no.
Escape character is '^]'.
220 alpha.domain.no ESMTP Postfix (Ubuntu)
EHLO domain.net
250-alpha.domain.no
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
**250-STARTTLS**
250-AUTH PLAIN LOGIN
250-AUTH=PLAIN LOGIN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250-DSN
250-SMTPUTF8
250 CHUNKING
1 Like