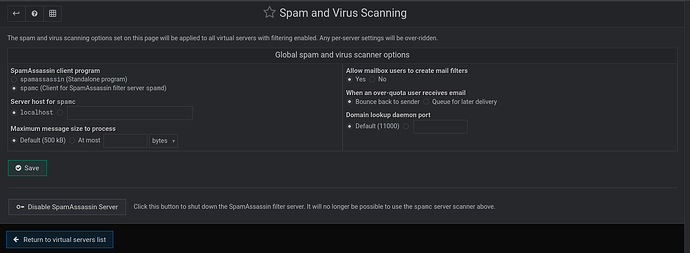
I just moved the first users over to my Virtualmin server and SpamAssassin as it is configured by default on Debian 12 is definitely not hitting enough of the spam – one client is getting inundated by dozens of messages an hour that the old filter (ASSP) was able to catch.
So, I’ve tried to accumulate some tweaks to the server (while trying not to break anything Virtualmin automates) to see if I could stem the tide. So far it isn’t enough, so I was hoping to share what I’ve done and see if there’s some obvious things I’m missing. (The biggest one, I suspect, was suggested to me in another thread on here – postscreen – but I’m trying to get my head around how to use it without messing up general user usage of SMTP, etc.)
Any tips on what seems to work to (relatively aggressively) fight spam, I’m all ears. A lot of threads I’ve found on here or elsewhere seem to be from many years ago, with links to additions to SpamAssassin that are no longer supported.
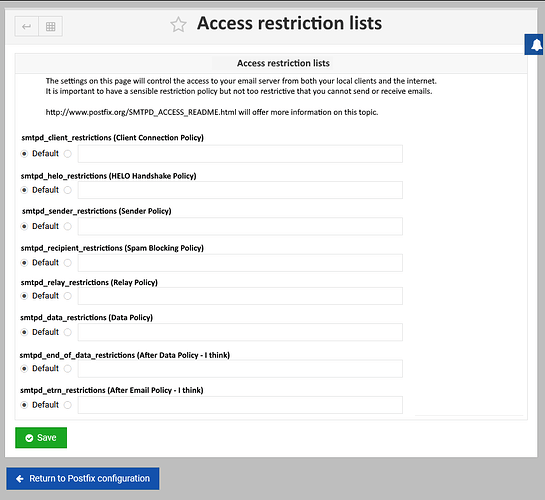
Here’s what I’ve done so far. In postfix, I’ve added/enabled OpenDMARC, OpenDKIM, policyd-spf and two core RBLs:
smtpd_recipient_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_unauth_destination, check_policy_service unix:private/policyd-spf, check_policy_service inet:127.0.0.1:10023,
reject_rhsbl_helo dbl.spamhaus.org,
reject_rhsbl_reverse_client dbl.spamhaus.org,
reject_rhsbl_sender dbl.spamhaus.org,
permit_dnswl_client list.dnswl.org=127.0.[0..255].[1..3],
reject_rbl_client zen.spamhaus.org,
reject_rbl_client bl.spamcop.net
Jumping down the config a bit:
milter_default_action = accept
milter_protocol = 6
smtpd_milters = inet:127.0.0.1:8891,inet:127.0.0.1:8893
non_smtpd_milters = inet:127.0.0.1:8891,inet:127.0.0.1:8893
(I haven’t successfully verified OpenDMARC is working yet. The tests always seem to stop with OpenDKIM.)
And a few other seemingly wise filters:
smtpd_sender_restrictions =
permit_mynetworks
permit_sasl_authenticated
reject_unknown_reverse_client_hostname
reject_unknown_client_hostname
smtpd_helo_required = yes
smtpd_helo_restrictions =
permit_mynetworks
permit_sasl_authenticated
reject_invalid_helo_hostname
reject_non_fqdn_helo_hostname
reject_unknown_helo_hostname
On the SpamAssassin side, I compiled DCC and also installed Pyzor and Razor. I then added the following rules:
razor_config /etc/mail/spamassassin/.razor/razor-agent.conf
pyzor_options --homedir /etc/mail/spamassassin
#pyzor_add_header 1
use_dcc 1
# When using dccifd, socket will be search from dcc_home
dcc_home /var/dcc
dcc_timeout 8
# If not using dccifd, dccproc is used
dcc_path /usr/local/bin/dccproc
# RAZOR seem to be getting overruled by other parts of SA, so increase impact.
score RAZOR2_CHECK 2.0
score RAZOR2_CF_RANGE_51_100 3.0
score RAZOR2_CF_RANGE_41_50 2.5
score RAZOR2_CF_RANGE_31_40 2.0
score RAZOR2_CF_RANGE_21_30 1.5
score RAZOR2_CF_RANGE_11_20 1.0
score RAZOR2_CF_RANGE_1_10 0.5
# From https://www.linuxbabe.com/redhat/spamassassin-centos-rhel-block-email-spam
score PDS_FROM_2_EMAILS 3.0
score EMPTY_MESSAGE 3.5
score FREEMAIL_DISPTO 2.0
score FREEMAIL_FORGED_REPLYTO 3.5
score DKIM_ADSP_NXDOMAIN 5.0
score FORGED_GMAIL_RCVD 2.5
header CUSTOM_DMARC_FAIL Authentication-Results =~ /dmarc=fail/
describe CUSTOM_DMARC_FAIL This email failed DMARC check
score CUSTOM_DMARC_FAIL 3.0
body BOUNCE_MSG /(Undelivered Mail Returned to Sender|Undeliverable|Auto-Reply|Automatic reply)/i
describe BOUNCE_MSG Undelivered mail notifications or auto-reply messages
score BOUNCE_MSG -1.5
header RCVD_IN_BRBL eval:check_rbl('brbl-lastexternal', 'b.barracudacentral.org.', '127.0.0.2')
describe RCVD_IN_BRBL Received via relay listed in Barracuda RBL
score RCVD_IN_BRBL 1.0
tflags RCVD_IN_BRBL net
| SYSTEM INFORMATION | |
|---|---|
| OS type and version | Debian 12 |
| Webmin version | 2.111 |
| Virtualmin version | 7.20.1 |
| Webserver version | NGINX 1.18.0/Apache 2.4.52 |
| Related packages | DCC, Pyzor, Razor, OpenDMARC, OpenDKIM |