| SYSTEM INFORMATION | |
|---|---|
| Ubuntu Linux 18.04.6 | REQUIRED |
| Webmin 2.100, | |
| Virtualmin version 7.7 | REQUIRED |
I have CSF, CLAMAV, Spamassassin installed
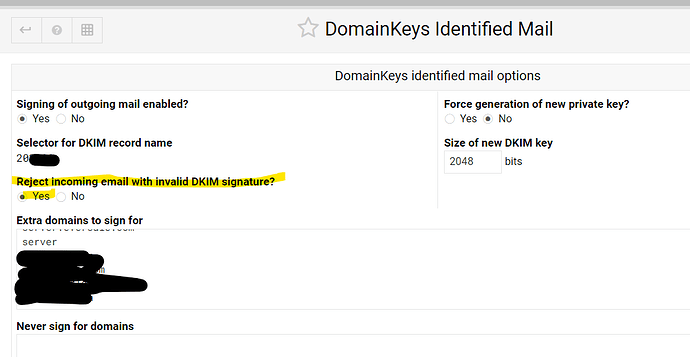
separate (external) DNS, with DKIM / domainkey, dmarc, spf records.
mxtoolbox says all 3 are correct
I have changed passwords for root, and all email accounts
CLAMav had found a virus prior, but today is clear, and yet still more spoof email
I removed only 5.x and 7.x PHP, now running 8.1 - I thought it was PHP script vulnerability
I cannot stop my server sending spam
i see in my own inbox email spoofed by external sender as sent my me
I click on the header and see the email send from external source (see below)
i can stop them for a while by blocking their IP address
the email header says the DKIM is failed, so how does it get through ?
what log can show me who this is ?
so how can i stop this ?
Return-Path: <>
X-Original-To: info@abc.com
Delivered-To: xyz-abc.com@localhost.localdomain
Received: by server.abc.com (Postfix)
id 46D43B1608; Wed, 26 Jul 2023 13:31:01 +0000 (UTC)
Delivered-To: info-abc.com@localhost.localdomain
Received: from dcacinc.com (unknown [45.132.18.248])
by server.abc.com (Postfix) with ESMTP id D4B45B15D7
for info@abc.com; Wed, 26 Jul 2023 13:31:00 +0000 (UTC)
Authentication-Results: server.abc.com;
dkim=fail reason=“signature verification failed” (2048-bit key; unprotected) header.d=aol.com header.i=@aol.com header.b=“og8IRrhz”;
dkim-atps=neutral
Received: by 2002:a05:6022:419e:b0:44:32db:72ed with SMTP id c30csp259366laa;
Wed, 26 Jul 2023 05:27:49 -0700 (PDT)
X-Google-Smtp-Source: APBJJlHuZVqJLPqHsFEeJP1Gz5r2NzYnm4V+UFeMXwAWAthRG8HONhNiX9G5DRTEeYPt1GfbUj0c
X-Received: by 2002:a05:620a:2a0b:b0:768:2b02:d41 with SMTP id o11-20020a05620a2a0b00b007682b020d41mr2519469qkp.57.1690374468860;
Wed, 26 Jul 2023 05:27:48 -0700 (PDT)
ARC-Seal: i=1; a=rsa-sha256; t=1690374468; cv=none;
d=google.com; s=arc-20160816;
b=Xb0lkn0dNkD1V4xPSFFvAEd46Ufe5lFD1TxXwu/oNJcGMcIiucuJHoR/hZ/x9jxI9w
Udzz9BnAwQOBf/ehIwJsO2hCMDObp34Dd6D1Pd0CaR6M2mNFYZ26UOb/EqTcDCGvd0+E
Gm99cdzQy2ILr38jE+gIF2v7d0li+awWtiFkmt7bAZRTtwlW0MuwtyoVoUobjUGTv4Sx
yFKTMv3thi0YBqqNb60B9ukSUUKWCEavflXNsZMR/Yuh7CEbA8tBO8tJK1wUni6afdrB
+sf2wJt/VHmqFFV1uxKmcfzJfV4CWfCLKHAdj9lXyRlsfS7dWaOQ9+dAB34UYIpC44VQ
L0Mw==
ARC-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed; d=google.com; s=arc-20160816;
h=mime-version:subject:references:in-reply-to:message-id:to:from:date
:dkim-signature;
bh=9CaJcABoSJ3Y5lrB6ZBgwoEg/MuJi3tVa6htKxkH4ik=;
fh=L8Cjpnf7WAnb36w845cXirL8nff2NdMyffZDlRztYgA=;
b=DwDADEq2SK4lt9lWgD9GkRoZWwUdRC8BFwBJZt8xSa2jG9qUesu0h9sQnggcmxIWSm
fgEh4x/FV9k0Op7ZIGD9bZiWfVjsL0c8vDe0oer77lh5Va679foeF2tDjQs/1IsqaITq
QnRsTmSWBAHrormbiHBbSFVJVcLf9QUcvwk3TPMMebyhsNeGywf7SjzJqPHKkcqfIC4Q
ySPVG0vySKEE2UWCvYdN+k0eteW8kBlBQw9/wlkOec2Be3VNVvukgmsQUjmPieLgfrqf
+OS4xvx1U6nscPRRzumLJCL9LdVNpAsVVfE/MsbwrK0VjmBJaxUchd4Xb75wXdHs2Ogo
EDWg==
ARC-Authentication-Results: i=1; mx.google.com;
dkim=pass header.i=@aol.com header.s=a2048 header.b=og8IRrhz;
spf=pass (google.com: domain of info@abc.com designates 66.163.185.206 as permitted sender) smtp.mailfrom=info@abc.com;
dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=aol.com
Received: from sonic321-25.consmr.mail.ne1.yahoo.com (sonic321-25.consmr.mail.ne1.yahoo.com. [66.163.185.206])
by mx.google.com with ESMTPS id f10-20020a05622a104a00b00403c7a46698si8056971qte.440.2023.07.26.05.27.48
for info@abc.com
(version=TLS1_3 cipher=TLS_AES_128_GCM_SHA256 bits=128/128);
Wed, 26 Jul 2023 05:27:48 -0700 (PDT)
Received-SPF: pass (google.com: domain of info@abc.com designates 66.163.185.206 as permitted sender) client-ip=66.163.185.206;
Authentication-Results: mx.google.com;
dkim=pass header.i=@aol.com header.s=a2048 header.b=og8IRrhz;
spf=pass (google.com: domain of info@abc.com designates 66.163.185.206 as permitted sender) smtp.mailfrom=info@abc.com;
dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=aol.com
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=aol.com; s=a2048; t=1690374468; bh=9CaJcABoSJ3Y5lrB6ZBgwoEg/MuJi3tVa6htKxkH4ik=; h=Date:From:To:In-Reply-To:References:Subject:From:Subject:Reply-To; …
…
…
V7 wow–
X-Sonic-MF: info@abc.com
X-Sonic-ID: 7913b128-550d-4559-8ca4-085a9aa835e9
Received: from sonic.gate.mail.ne1.yahoo.com by sonic321.consmr.mail.ne1.yahoo.com with HTTP; Wed, 26 Jul 2023 12:27:48 +0000
Date: Wed, 26 Jul 2023 15:30:46 +0200
From: Shell 2022 info@abc.com
To: Shell 2022 info@abc.com
Message-ID: 1165396162.5485103.1690163815330@mail.yahoo.com
Subject: you have (1) Shell Reward ready to claim !
MIME-Version: 1.0
Content-Type: multipart/alternative; boundary=“----=_Part_5447617_1191263717.1690374466117”
X-Mailer: WebService/1.1.21647 AolMailNorrin
from the mail log:
Jul 26 13:31:01 server postfix/qmgr[3795]: D4B45B15D7: removed
Jul 26 13:31:01 server postfix/local[20806]: D4B45B15D7: to=info-abc.com@localhost.localdomain, orig_to=info@abc.com, relay=local, delay=0.45, delays=0.42/0/0/0.03, dsn=2.0.0, status=sent (forwarded as 46D43B1608)
Jul 26 13:31:01 server postfix/local[20806]: D4B45B15D7: to=info-abc.com@localhost.localdomain, orig_to=info@abc.com, relay=local, delay=0.44, delays=0.42/0/0/0.02, dsn=2.0.0, status=sent (delivered to command: /usr/bin/procmail -a “$EXTENSION” DEFAULT=$HOME/Maildir/ MAILDIR=$HOME/Maildir)
Jul 26 13:31:01 server postfix/qmgr[3795]: D4B45B15D7: from=<>, size=12960, nrcpt=1 (queue active)
Jul 26 13:31:01 server opendkim[381]: D4B45B15D7: bad signature data
Jul 26 13:31:01 server opendkim[381]: D4B45B15D7: s=a2048 d=aol.com SSL error:04091068:rsa routines:int_rsa_verify:bad signature
Jul 26 13:31:01 server opendkim[381]: D4B45B15D7: external host [45.132.18.248] attempted to send as abc.com
Jul 26 13:31:01 server postfix/cleanup[20663]: D4B45B15D7: message-id=1165396162.5485103.1690163815330@mail.yahoo.com
Jul 26 13:31:00 server postfix/smtpd[20797]: D4B45B15D7: client=unknown[45.132.18.248]