hello friends please my port 25 always blocked by the provider because of spam I don’t know how to protect myself please if anyone can help me or someone has an idea thank you
So? Take it up with your provider - you chose the provider!
Cannot see why this has anything to do with Virtualmin ![]()
@Stegan You are right. This is definitely not a Virtualmin issue.
hello friends and thank you very much for your support
I will rephrase my request
my request is that I am a beginner on virtualmin because the first time I tried with Cpanel for me virtualmin is new so I do not know where I should go to control the sending of SMTP or port 25 so for for me virtualmin it is not a responsible but it is the tools where I must put my parameters or my configuration
thank you again if you want to help me please show me where I should go to give limits for each email for example the number of emails sent per hour or per day or something to control port 25 thank you again
Hi, please excuse the abruptness of my previous response. Language is a beautiful thing → it would be so much simpler if everyone across the globe understood the same language, but we don’t and sometimes translators don’t really help much.
I am hoping that your post here does not relate to your other recent posts regarding the problems with port 25 as I think that was answered.
We can see from other topics that you are new to Virtualmin. Therefore, from a forum perspective they really belong in “Help” and then ideally only after reading the documentation.
You do not need to control port 25 it should be open.
If I understand the key part of your question it is:
How to limit the number of emails sent by a user ?
Which is quite different from the title of this topic. Yes?
I believe what you want is under Virtualmin -> Email Settings -> Mail Rate Limiting though I’m not sure. I have never had the need to impose this restriction on any of my users.
Yes MR on my side I am sure that google translation does not do the trick but for the title I confirm I want to know how to configure the Spam and Virus Scanning rebrick because it is spam which increases the traffic output through port 25 then I confirm that my question is correct and the title too and thank you again Mr
So you are concerned with mail coming in to the server not your user’s sending “spam” out. ?
That is a job for Virtualmin -> Mail Options -> SpamAssassin Configuration
For which I strongly suggest reading as much as you can about. It is not a simple task.
Though if you know what you are doing. Virtualmin makes it simpler.
Virus detection is a complete;y different matter and in my limited experience not worth a candle. ClamAV is the route to go but it can bring your VM to a standstill as it uses so much processor time and memory.
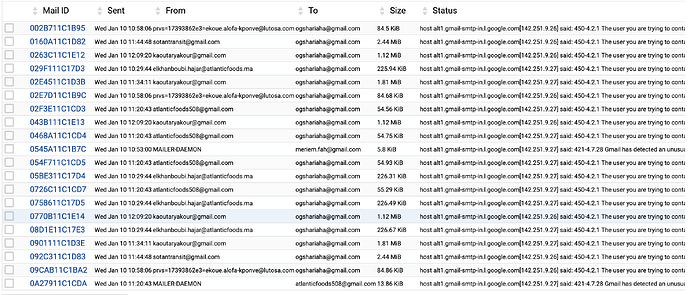
I found it at a friend’s house what I should do next for the info I found an email address coming out of the server 5000 emails per min for this the provider deactivates port 25 can I activate this option to no longer have his worries thank you
with 5000 per min ![]() I would go to:
I would go to:
select the really bad culprits from your list (eg atlanticfoods508@gmail.com) and put them in the “always denied” list.
Do it for one and see if it stops that one coming in - then fill the list with the others.
I have no idea why you are attracting so many, some appear to be genuine so I would add them with caution. This list will class them all as spam so you could end up no getting one even one. So something like *@gail would be really silly!
hello dear mr really it is practical the tip that you showed me but there is a problem for this tip the emails displayed in the photo are not incoming emails they are outgoing emails otherwise it does not pose a problem for me if they come in I will classify them as spam or with the tool that you showed me I confirm that the photo is emails in a sort of inexplicable way I can say for example that maybe someone works with outlouk and his pc already contaminated with spam which has control over the email and like that it has total access to SMTP and of course it can send emails from the server but with a referent address
firstly you should have sensible limits set to prevent this
Virtualmin → Mail Rate Limiting → Rate limiting enabled? = Yes
Virtualmin → Mail Rate Limiting → Global message limit: 50 per hour (but less for now)
Who is sending
Webmin → Servers → Postfix Mail Server → Mail Queue.
read this - Can I find out who is broadcasting emails on my server? [#14192] | Virtualmin
or
Edit a message and see what account is sending the email.
Logs
Webmin → Systems → System Logs
Webmin → Systems → System Logs Viewer → File /var/log/mail.log
Also on pro
Virtualmin → logs and reports → Search mail logs
So we are back to my original understanding of the problem , and the question I threw back in post #4.
Though it is probably worse. You have someone using one of your user’s accounts to relay “spam”.
I find the best solution to this type of problem is to delete the account. grant the user a new account, but not before educating the user not to let the door open. (allow their email to be hijacked) - if they have been careless with their password or simply loaded a virus in their email then who knows what monster they have let in to the system.
Rate limiting would of course be a simple step but I’m not sure that is going to be effective enough in this case. They are still being generated and for sure will be using up bandwidth and your resources not to mention the real possibility of ypur IP being identified as a spam source. The folk who do this sell on/give away to others an IP/email that has been hijacked there is sadly a whole industry out there taking advantage of any poor security.
That’s not the problem and it won’t help.
The problem is OP has a web app that allows anyone to send through their server or an exploited user account that is sending the mail. Virtualmin and SpamAssassin can’t solve that (though it is possible to rate limit sending, that’s not a solution that’s just a slight mitigation). The real problem is an exploited application or user, and the real solution is fixing that app or disabling that exploited user.
That is what I suggested back in #4 but we moved on from that solution due to unclear response to my question about incoming vs outgoing.
I believe we now have it confirmed as outgoing (ie a user in the VS relaying)
which is why I was suggesting killing the user as a solution. that is the user’s email account not literally ![]()
Though you are right, this is a deeper problem (let me guess, because there has been no mention here of any app being involved) it is a WordPress app!
hello MR joe and MR slogan what I just said to myself it makes sense like that I am going to stop the imoragy once and for all but is it better to limit emails to a fair number per day like that or places of delete it gives him an option to send for example 200 emails per day when he exceeds the number the box is blocked like that he will intervene and he tries either to delete it or change the password or wait until the next day
can you show me how to limit an email for example for a specific number of emails per day thank you very much for your support really you are always there for me
Hi Mr I haven’t seen your message thank you very much I’m going to try this solution it seemed great to me please can I specify the account on which I will apply this rule
You can as well required users to change password. that should fix it in the case that there is a vulnerable user.
j ai deja essayer ca ![]()
siaradwch yn Saesneg os gwelwch yn dda, I tend to do that when replying to threads
I forgot to translate sorry