but this hostname is not hosted any where…
Where web-server then is running for this domain?
Using DNS validation:
Requesting a new certificate for q7.btcloud.eu, using DNS validation …
… request failed : Neither DNS zone q7.btcloud.eu or any of its sub-domains exist on this system
Using Other directory:
Failed to request certificate : Website document directory does not exist
I know there is not hosting for this url its only for accessing the server ip, and only A Record has been entered in domain registrar panel.
I have no idea what you’re asking nor what trying to achieve, sorry.
You can not request SSL certificate for an IP address.
You could, however, use custom generated SSL certificate, and secure connection between you (user) and your server.
I have added a DNS Master Zone in Webmin regarding q7.btcloud.eu and add A Record and then try to install the Letsencrypt SSL certificate as per tutorial and result is as follows:
Requesting a new certificate for q7.btcloud.eu, using DNS validation …
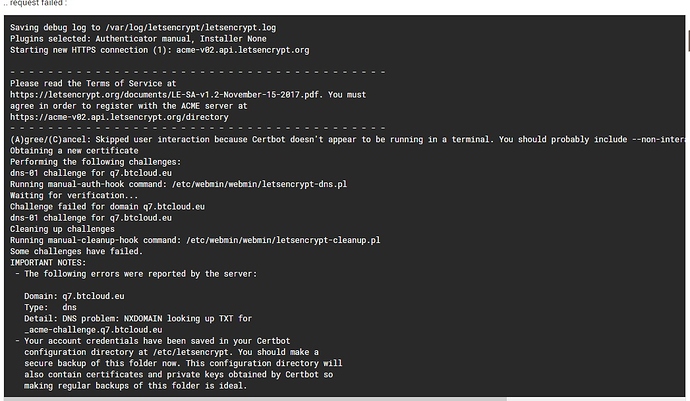
… request failed :
Okay, that’s better.
What is the output of /var/log/letsencrypt/letsencrypt.log.
How did you install Virtualmin on your CentOS 7 machine?
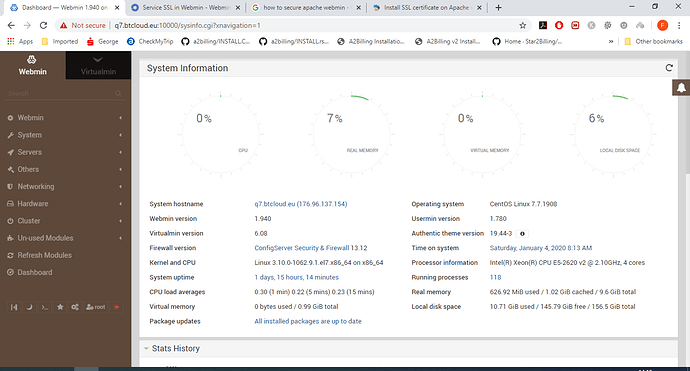
Can you show me the way your panel looks using screenshot?
What is Webmin and Virtualmin version do you have installed there?
/var/log/letsencrypt/letsencrypt.log
2020-01-04 07:42:38,242:DEBUG:certbot._internal.main:certbot version: 1.0.0
2020-01-04 07:42:38,242:DEBUG:certbot._internal.main:Arguments: ['--manual', '-d', 'q7.btcloud.eu', '--preferred-challenges=dns', '--manual-auth-hook', '/etc/webmin/webmin/letsencrypt-dns.pl', '--manual-cleanup-hook', '/etc/webmin/webmin/letsencrypt-cleanup.pl', '--duplicate', '--force-renewal', '--manual-public-ip-logging-ok', '--config', '/tmp/.webmin/438799_8720_2_letsencrypt.cgi', '--rsa-key-size', '2048', '--cert-name', 'q7.btcloud.eu']
2020-01-04 07:42:38,242:DEBUG:certbot._internal.main:Discovered plugins: PluginsRegistry(PluginEntryPoint#manual,PluginEntryPoint#null,PluginEntryPoint#standalone,PluginEntryPoint#webroot)
2020-01-04 07:42:38,307:DEBUG:certbot._internal.log:Root logging level set at 20
2020-01-04 07:42:38,307:INFO:certbot._internal.log:Saving debug log to /var/log/letsencrypt/letsencrypt.log
2020-01-04 07:42:38,309:DEBUG:certbot._internal.plugins.selection:Requested authenticator manual and installer None
2020-01-04 07:42:38,312:DEBUG:certbot._internal.plugins.selection:Single candidate plugin: * manual
Description: Manual configuration or run your own shell scripts
Interfaces: IAuthenticator, IPlugin
Entry point: manual = certbot._internal.plugins.manual:Authenticator
Initialized: <certbot._internal.plugins.manual.Authenticator object at 0x7fde16e02990>
Prep: True
2020-01-04 07:42:38,313:DEBUG:certbot._internal.plugins.selection:Selected authenticator <certbot._internal.plugins.manual.Authenticator object at 0x7fde16e02990> and installer None
2020-01-04 07:42:38,313:INFO:certbot._internal.plugins.selection:Plugins selected: Authenticator manual, Installer None
2020-01-04 07:42:38,453:DEBUG:acme.client:Sending GET request to https://acme-v02.api.letsencrypt.org/directory.
2020-01-04 07:42:38,466:INFO:urllib3.connectionpool:Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org
2020-01-04 07:42:40,267:DEBUG:urllib3.connectionpool:"GET /directory HTTP/1.1" 200 658
2020-01-04 07:42:40,269:DEBUG:acme.client:Received response:
HTTP 200
content-length: 658
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
cache-control: public, max-age=0, no-cache
date: Sat, 04 Jan 2020 12:42:43 GMT
x-frame-options: DENY
content-type: application/json
{
"iy8k5uZ45Zw": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417",
"keyChange": "https://acme-v02.api.letsencrypt.org/acme/key-change",
"meta": {
"caaIdentities": [
"letsencrypt.org"
],
"termsOfService": "https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf",
"website": "https://letsencrypt.org"
},
"newAccount": "https://acme-v02.api.letsencrypt.org/acme/new-acct",
"newNonce": "https://acme-v02.api.letsencrypt.org/acme/new-nonce",
"newOrder": "https://acme-v02.api.letsencrypt.org/acme/new-order",
"revokeCert": "https://acme-v02.api.letsencrypt.org/acme/revoke-cert"
}
2020-01-04 07:42:40,272:DEBUG:acme.client:Requesting fresh nonce
2020-01-04 07:42:40,272:DEBUG:acme.client:Sending HEAD request to https://acme-v02.api.letsencrypt.org/acme/new-nonce.
2020-01-04 07:42:40,427:DEBUG:urllib3.connectionpool:"HEAD /acme/new-nonce HTTP/1.1" 200 0
2020-01-04 07:42:40,429:DEBUG:acme.client:Received response:
HTTP 200
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
cache-control: public, max-age=0, no-cache
date: Sat, 04 Jan 2020 12:42:44 GMT
x-frame-options: DENY
replay-nonce: 0001Flq0bLKxa0PkFtXlnXKFODI3dmmRi3ta4UHNH0gBoSk
2020-01-04 07:42:40,429:DEBUG:acme.client:Storing nonce: 0001Flq0bLKxa0PkFtXlnXKFODI3dmmRi3ta4UHNH0gBoSk
2020-01-04 07:42:40,430:DEBUG:acme.client:JWS payload:
{
"termsOfServiceAgreed": true,
"resource": "new-reg",
"contact": [
"mailto:root@q7.btcloud.eu"
]
}
2020-01-04 07:42:40,439:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/new-acct:
{
"protected": "eyJub25jZSI6ICIwMDAxRmxxMGJMS3hhMFBrRnRYbG5YS0ZPREkzZG1tUmkzdGE0VUhOSDBnQm9TayIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvbmV3LWFjY3QiLCAiandrIjogeyJlIjogIkFRQUIiLCAia3R5IjogIlJTQSIsICJuIjogIm91U1RsWTFsUWRZVzYzb2trS2hWcHNMaDcxbVI3LXFuekZ2VUpwYTdvR3F2Um9YdGp0cFFmZnRUcFlOeHBEUURzdVV6ak10RTJHR3dha0lvcEM4M1RvZ3JPekdmUlRZa0t1ZEVFYkNHVy1WQXppaWsyQm00c2ZVSnhLLTB4LTdFd3ZZamtUMnAyZUdPMU1vUWFfTkJkYjB5YVItS2dHUDJ5TzFKamwyNTNzZFJidzZWa1BhQVF2akRvM29jUVpRSDZNeGtqWllBOURTQ0JqZ2NfVzgwWjZSUGROYV9FMGNiUkRsaExSeUFCQ0hCZUhzWnhXS21Ma0NwVVVlSmZCV0dpWGRJOWk4blYzOGdlenVoR1JaSTRPN0lIZ2QtNlZOdDRfTjVPeS1JcUY3OHoyTjBWU2sza01VUlJub1BPZUhrZ3cySVEzdW9jclROdTREYTVlXzh1USJ9LCAiYWxnIjogIlJTMjU2In0",
"payload": "ewogICJ0ZXJtc09mU2VydmljZUFncmVlZCI6IHRydWUsIAogICJyZXNvdXJjZSI6ICJuZXctcmVnIiwgCiAgImNvbnRhY3QiOiBbCiAgICAibWFpbHRvOnJvb3RAcTcuYnRjbG91ZC5ldSIKICBdCn0",
"signature": "QKzZhpsTc9I3UxOuJoX4QTq3n9hw1lzdlxR7Aw0ayduuzwDzDAL4eIx7YU5RFxiWJbTBQ76WpEIb-S7f9oRcNqWT7wniwHPNT8FVPJo9ixudlK62LWYZzZiKyY3kUDfBBQpG1bzJ-ZEuMl26EiW5zumqOn36vdRf7jXrGYD9Jp4EH8KBWSp4kSLopKlxU3S3r0dhGk--JBbElVKFeoe66FKI4sLsnpXt5_Ud9iwQBHtOGSKiRWlMxD29qJcg1JyF_kYlfEihGO3I2C0ZixVe37BYY99tWk-CBVzcnXQLjbDn6-uRmkpDPMllYISgdhV4ESLEy6sj9R_l250WcWxPtg"
}
2020-01-04 07:42:40,731:DEBUG:urllib3.connectionpool:"POST /acme/new-acct HTTP/1.1" 201 568
2020-01-04 07:42:40,732:DEBUG:acme.client:Received response:
HTTP 201
content-length: 568
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index", <https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf>;rel="terms-of-service"
location: https://acme-v02.api.letsencrypt.org/acme/acct/75133877
boulder-requester: 75133877
date: Sat, 04 Jan 2020 12:42:44 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 0001o6-V4BQafBsjPqIAAcIJv8ZaX_uyXIUv-SUMlZOk4-4
{
"key": {
"kty": "RSA",
"n": "ouSTlY1lQdYW63okkKhVpsLh71mR7-qnzFvUJpa7oGqvRoXtjtpQfftTpYNxpDQDsuUzjMtE2GGwakIopC83TogrOzGfRTYkKudEEbCGW-VAziik2Bm4sfUJxK-0x-7EwvYjkT2p2eGO1MoQa_NBdb0yaR-KgGP2yO1Jjl253sdRbw6VkPaAQvjDo3ocQZQH6MxkjZYA9DSCBjgc_W80Z6RPdNa_E0cbRDlhLRyABCHBeHsZxWKmLkCpUUeJfBWGiXdI9i8nV38gezuhGRZI4O7IHgd-6VNt4_N5Oy-IqF78z2N0VSk3kMURRnoPOeHkgw2IQ3uocrTNu4Da5e_8uQ",
"e": "AQAB"
},
"contact": [
"mailto:root@q7.btcloud.eu"
],
"initialIp": "2a0d:5940:8:1d::be5c",
"createdAt": "2020-01-04T12:42:44.396093879Z",
"status": "valid"
}
2020-01-04 07:42:40,733:DEBUG:acme.client:Storing nonce: 0001o6-V4BQafBsjPqIAAcIJv8ZaX_uyXIUv-SUMlZOk4-4
2020-01-04 07:42:40,735:DEBUG:certbot._internal.reporter:Reporting to user: Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal.
2020-01-04 07:42:40,738:WARNING:certbot.display.util:Skipped user interaction because Certbot doesn't appear to be running in a terminal. You should probably include --non-interactive or --force-interactive on the command line.
2020-01-04 07:42:40,738:DEBUG:certbot.display.util:Falling back to default False for the prompt:
Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom.
2020-01-04 07:42:40,739:DEBUG:certbot._internal.main:Picked account: <Account(RegistrationResource(body=Registration(status=u'valid', terms_of_service_agreed=None, agreement=None, only_return_existing=None, contact=(u'mailto:root@q7.btcloud.eu',), key=JWKRSA(key=<ComparableRSAKey(<cryptography.hazmat.backends.openssl.rsa._RSAPublicKey object at 0x7fde169bac10>)>), external_account_binding=None), uri='https://acme-v02.api.letsencrypt.org/acme/acct/75133877', new_authzr_uri=None, terms_of_service='https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf'), 2e765caa3f50ad4c5b151dcffb07c9ee, Meta(creation_host='q7.btcloud.eu', creation_dt=datetime.datetime(2020, 1, 4, 12, 42, 40, tzinfo=<UTC>)))>
2020-01-04 07:42:40,740:INFO:certbot._internal.main:Obtaining a new certificate
2020-01-04 07:42:40,915:DEBUG:certbot.crypto_util:Generating key (2048 bits): /etc/letsencrypt/keys/0000_key-certbot.pem
2020-01-04 07:42:40,919:DEBUG:certbot.crypto_util:Creating CSR: /etc/letsencrypt/csr/0000_csr-certbot.pem
2020-01-04 07:42:40,921:DEBUG:acme.client:JWS payload:
{
"identifiers": [
{
"type": "dns",
"value": "q7.btcloud.eu"
}
]
}
2020-01-04 07:42:40,924:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/new-order:
{
"protected": "eyJub25jZSI6ICIwMDAxbzYtVjRCUWFmQnNqUHFJQUFjSUp2OFphWF91eVhJVXYtU1VNbFpPazQtNCIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvbmV3LW9yZGVyIiwgImtpZCI6ICJodHRwczovL2FjbWUtdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hY2N0Lzc1MTMzODc3IiwgImFsZyI6ICJSUzI1NiJ9",
"payload": "ewogICJpZGVudGlmaWVycyI6IFsKICAgIHsKICAgICAgInR5cGUiOiAiZG5zIiwgCiAgICAgICJ2YWx1ZSI6ICJxNy5idGNsb3VkLmV1IgogICAgfQogIF0KfQ",
"signature": "Y9R53x2_pZEYEDBbqj33524bxs4xZwAn3PBTlQVP7FxBSBIY5tOhfC1mDiQ_VTo_tSwuU8FwmVXeq8lqWwj-G6ujBMbF0Bo2M-Zd3037BPSJ_UAnDm9GJeMhOof-3Exk-G2zVxwO1uru8FppNgoNs2YOCuLZrnh6zJ_gEiE0sC2l8V_KpB6VDoDDwiOOSLesxh4sRIgJZ6VBRqq3rS5VC5LUxD8fXooz3RT1qzIAH_IDO8-ulNeqHJWr3V5628yIwKMwcaj-n_d3WrdurUwaL3yuP2WE16nMLfBR5uIKo707I5sVeeg2mV8vjC-52DW5i8u2dt35sDzMrLMLIH5Oow"
}
2020-01-04 07:42:41,147:DEBUG:urllib3.connectionpool:"POST /acme/new-order HTTP/1.1" 201 343
2020-01-04 07:42:41,149:DEBUG:acme.client:Received response:
HTTP 201
content-length: 343
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
location: https://acme-v02.api.letsencrypt.org/acme/order/75133877/1936378496
boulder-requester: 75133877
date: Sat, 04 Jan 2020 12:42:44 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 0001VVQK4WJg2OYZb3aCMRWKGrO8_LxASu1IXerSh952Bis
{
"status": "pending",
"expires": "2020-01-11T12:42:44.804040484Z",
"identifiers": [
{
"type": "dns",
"value": "q7.btcloud.eu"
}
],
"authorizations": [
"https://acme-v02.api.letsencrypt.org/acme/authz-v3/2101523180"
],
"finalize": "https://acme-v02.api.letsencrypt.org/acme/finalize/75133877/1936378496"
}
2020-01-04 07:42:41,149:DEBUG:acme.client:Storing nonce: 0001VVQK4WJg2OYZb3aCMRWKGrO8_LxASu1IXerSh952Bis
2020-01-04 07:42:41,153:DEBUG:acme.client:JWS payload:
2020-01-04 07:42:41,157:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/2101523180:
{
"protected": "eyJub25jZSI6ICIwMDAxVlZRSzRXSmcyT1laYjNhQ01SV0tHck84X0x4QVN1MUlYZXJTaDk1MkJpcyIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYXV0aHotdjMvMjEwMTUyMzE4MCIsICJraWQiOiAiaHR0cHM6Ly9hY21lLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC83NTEzMzg3NyIsICJhbGciOiAiUlMyNTYifQ",
"payload": "",
"signature": "GZ1Xfnyh2T2bhWoLmR_ibPYLTdHX5bE6TmYdA_VbQUvTKKT0aZmsPP_1bIJbcGvef5jhffxa-GvVM1mdZiBfmsMo9YMa-pd6zaOfkt3zszVm-u-nx1gXQIGARK8DNHvF7iTeYO2OQZG-eb-RQIszyrwM5ZTrs-W2GNMjsPs_3T3oGpczkcth_8M55gAZ4qPJCPRqga6zNCAYI9ySaeA2ADH3Rbg8GlwNe_bo8NfCkbh3YdUr7PzftUBlGez52JIqIjlrG3JdCjWCW6J_gKIWWVcNaGJC4fOA3M2k7T6DfADkmkDTGuA2J8_TFBefSNbIkDZUbVGO4z93Z3BUy5AQ_Q"
}
2020-01-04 07:42:41,315:DEBUG:urllib3.connectionpool:"POST /acme/authz-v3/2101523180 HTTP/1.1" 200 791
2020-01-04 07:42:41,316:DEBUG:acme.client:Received response:
HTTP 200
content-length: 791
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
boulder-requester: 75133877
date: Sat, 04 Jan 2020 12:42:44 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 0002-7YxpnAeB9i-IEbNx61ax1Fr02yH4ln7qOhSYjeTiPE
{
"identifier": {
"type": "dns",
"value": "q7.btcloud.eu"
},
"status": "pending",
"expires": "2020-01-11T12:42:44Z",
"challenges": [
{
"type": "http-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/2101523180/K9H-Gg",
"token": "YOhm6fQLCjhLSSCqXjrd_tcNAH-WiaAHhZ8N90TD23I"
},
{
"type": "dns-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/2101523180/3tU1YQ",
"token": "YOhm6fQLCjhLSSCqXjrd_tcNAH-WiaAHhZ8N90TD23I"
},
{
"type": "tls-alpn-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/2101523180/UjFkHA",
"token": "YOhm6fQLCjhLSSCqXjrd_tcNAH-WiaAHhZ8N90TD23I"
}
]
}
2020-01-04 07:42:41,317:DEBUG:acme.client:Storing nonce: 0002-7YxpnAeB9i-IEbNx61ax1Fr02yH4ln7qOhSYjeTiPE
2020-01-04 07:42:41,318:INFO:certbot._internal.auth_handler:Performing the following challenges:
2020-01-04 07:42:41,319:INFO:certbot._internal.auth_handler:dns-01 challenge for q7.btcloud.eu
2020-01-04 07:42:41,327:INFO:certbot._internal.hooks:Running manual-auth-hook command: /etc/webmin/webmin/letsencrypt-dns.pl
2020-01-04 07:42:56,619:INFO:certbot._internal.auth_handler:Waiting for verification...
2020-01-04 07:42:56,621:DEBUG:acme.client:JWS payload:
{
"type": "dns-01",
"resource": "challenge"
}
2020-01-04 07:42:56,626:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/chall-v3/2101523180/3tU1YQ:
{
"protected": "eyJub25jZSI6ICIwMDAyLTdZeHBuQWVCOWktSUViTng2MWF4MUZyMDJ5SDRsbjdxT2hTWWplVGlQRSIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvY2hhbGwtdjMvMjEwMTUyMzE4MC8zdFUxWVEiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvNzUxMzM4NzciLCAiYWxnIjogIlJTMjU2In0",
"payload": "ewogICJ0eXBlIjogImRucy0wMSIsIAogICJyZXNvdXJjZSI6ICJjaGFsbGVuZ2UiCn0",
"signature": "OHlRwXdZ_VnTDBjdhuIMLDJSbnkrQoo4kMaYjV8lUMO15TDk2SFezz2KDz20prCYbPlYeCIcrYn916W_dpTZndM8hmyZJIKnHlkmc4N4pLbCm3Kr9Ckk-nBwnvNJF9ev385fDm5jwJxnpodP7tKue3exUMppjM9RrgIupprzXsI5IRDHh8CJM3tF9aZ5yONVYXzvIeNrBp_Vwmxox7AvBz9VBsqMU9JcHLJ4z5G2OaYe_8V5DMwoaKKuSDibKBLa4BcP-ClF_-z7eWP5zntkx_T8Skp62nVCT_6VoLkTxFWwUn89qaV4p1MLvhaOKltXlkK0BtAyW7V5dgrcCV8jow"
}
2020-01-04 07:42:56,787:DEBUG:urllib3.connectionpool:"POST /acme/chall-v3/2101523180/3tU1YQ HTTP/1.1" 200 184
2020-01-04 07:42:56,789:DEBUG:acme.client:Received response:
HTTP 200
content-length: 184
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index", <https://acme-v02.api.letsencrypt.org/acme/authz-v3/2101523180>;rel="up"
location: https://acme-v02.api.letsencrypt.org/acme/chall-v3/2101523180/3tU1YQ
boulder-requester: 75133877
date: Sat, 04 Jan 2020 12:43:00 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 0002unp5LU5IX7tBxUMZUJGdeFCinJS1lDiR2guweEwwIcg
{
"type": "dns-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/2101523180/3tU1YQ",
"token": "YOhm6fQLCjhLSSCqXjrd_tcNAH-WiaAHhZ8N90TD23I"
}
2020-01-04 07:42:56,789:DEBUG:acme.client:Storing nonce: 0002unp5LU5IX7tBxUMZUJGdeFCinJS1lDiR2guweEwwIcg
2020-01-04 07:42:57,792:DEBUG:acme.client:JWS payload:
2020-01-04 07:42:57,797:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/2101523180:
{
"protected": "eyJub25jZSI6ICIwMDAydW5wNUxVNUlYN3RCeFVNWlVKR2RlRkNpbkpTMWxEaVIyZ3V3ZUV3d0ljZyIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYXV0aHotdjMvMjEwMTUyMzE4MCIsICJraWQiOiAiaHR0cHM6Ly9hY21lLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC83NTEzMzg3NyIsICJhbGciOiAiUlMyNTYifQ",
"payload": "",
"signature": "Kf4BU48Pjo1r-BvXFHXNSTwMBhKko4NPGayIDEMmIEdzfpGBFYcSmf5Dr8YzOHaeOlVxhVOoEEnN0vlsLLI4GiUE3lQJGpUFI_bSfHQoNbDRvQ8SoxwBeOENDKsHiCdljBT8F2DWrjvEJvVmjMZQ7GPGnxDubnd_5rBf4BLgUGsjYxqadmeyZR61hnQ4W1UTlUyUWaP5nlSTE0UeSbyv2cqiZDZnwVQ5Yl7o1Dm2ZktTXU6iYUroRiBF5iJ76N1ddhlUbDOpb-VX8iCdE0TJn_kVQ_O4JeLpHId6Mso5xYy-fg7xK6aJXrr9X6Adohm2m_2jaRK265rr4YUeI5BoKg"
}
2020-01-04 07:42:58,000:DEBUG:urllib3.connectionpool:"POST /acme/authz-v3/2101523180 HTTP/1.1" 200 555
2020-01-04 07:42:58,002:DEBUG:acme.client:Received response:
HTTP 200
content-length: 555
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
boulder-requester: 75133877
date: Sat, 04 Jan 2020 12:43:01 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 00025Y5choW0Agwz8bpYHrFGBo31q9hikMgatL_89m4j_90
{
"identifier": {
"type": "dns",
"value": "q7.btcloud.eu"
},
"status": "invalid",
"expires": "2020-01-11T12:42:44Z",
"challenges": [
{
"type": "dns-01",
"status": "invalid",
"error": {
"type": "urn:ietf:params:acme:error:dns",
"detail": "DNS problem: NXDOMAIN looking up TXT for _acme-challenge.q7.btcloud.eu",
"status": 400
},
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/2101523180/3tU1YQ",
"token": "YOhm6fQLCjhLSSCqXjrd_tcNAH-WiaAHhZ8N90TD23I"
}
]
}
2020-01-04 07:42:58,003:DEBUG:acme.client:Storing nonce: 00025Y5choW0Agwz8bpYHrFGBo31q9hikMgatL_89m4j_90
2020-01-04 07:42:58,004:WARNING:certbot._internal.auth_handler:Challenge failed for domain q7.btcloud.eu
2020-01-04 07:42:58,005:INFO:certbot._internal.auth_handler:dns-01 challenge for q7.btcloud.eu
2020-01-04 07:42:58,005:DEBUG:certbot._internal.reporter:Reporting to user: The following errors were reported by the server:
Domain: q7.btcloud.eu
Type: dns
Detail: DNS problem: NXDOMAIN looking up TXT for _acme-challenge.q7.btcloud.eu
2020-01-04 07:42:58,006:DEBUG:certbot._internal.error_handler:Encountered exception:
Traceback (most recent call last):
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 91, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 180, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
AuthorizationError: Some challenges have failed.
2020-01-04 07:42:58,007:DEBUG:certbot._internal.error_handler:Calling registered functions
2020-01-04 07:42:58,007:INFO:certbot._internal.auth_handler:Cleaning up challenges
2020-01-04 07:42:58,008:INFO:certbot._internal.hooks:Running manual-cleanup-hook command: /etc/webmin/webmin/letsencrypt-cleanup.pl
2020-01-04 07:43:01,600:DEBUG:certbot._internal.log:Exiting abnormally:
Traceback (most recent call last):
File "/bin/letsencrypt", line 9, in <module>
load_entry_point('certbot==1.0.0', 'console_scripts', 'certbot')()
File "/usr/lib/python2.7/site-packages/certbot/main.py", line 14, in main
return internal_main.main(cli_args)
File "/usr/lib/python2.7/site-packages/certbot/_internal/main.py", line 1350, in main
return config.func(config, plugins)
File "/usr/lib/python2.7/site-packages/certbot/_internal/main.py", line 1237, in certonly
lineage = _get_and_save_cert(le_client, config, domains, certname, lineage)
File "/usr/lib/python2.7/site-packages/certbot/_internal/main.py", line 121, in _get_and_save_cert
lineage = le_client.obtain_and_enroll_certificate(domains, certname)
File "/usr/lib/python2.7/site-packages/certbot/_internal/client.py", line 416, in obtain_and_enroll_certificate
cert, chain, key, _ = self.obtain_certificate(domains)
File "/usr/lib/python2.7/site-packages/certbot/_internal/client.py", line 347, in obtain_certificate
orderr = self._get_order_and_authorizations(csr.data, self.config.allow_subset_of_names)
File "/usr/lib/python2.7/site-packages/certbot/_internal/client.py", line 395, in _get_order_and_authorizations
authzr = self.auth_handler.handle_authorizations(orderr, best_effort)
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 91, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 180, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
AuthorizationError: Some challenges have failed.
Did you install Virtualmin using install.sh script? Can you switch to Virtualmin tab, and make a screenshot of it?
In short, Webmin needs an access, either to DNS server (should be hosted on the same machine) for passing DNS challenge, or web-server (Apache) for passing HTTP challenge.
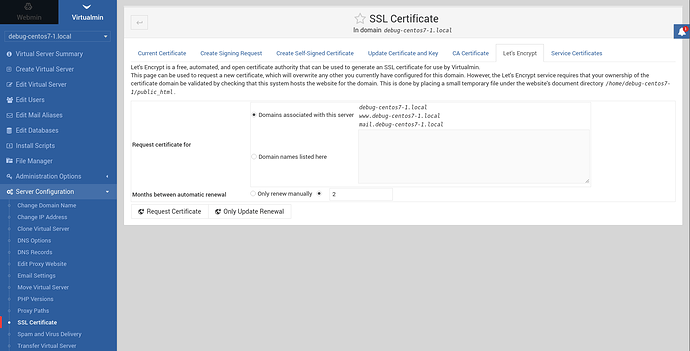
If there are changes that you made manually to your DNS configuration, just revert it, and add a virtual server using Virtualmin tab. Then request certificate under Server Configuration/SSL Certificate/Let’s Encrypt.
I am taking a closer look at DNS validation and if it’s done/works right for default setups.
Latest Webmin can handle DNS validation without an issue.
I have already created A Record in my domain registrar
Is DNS server for domain and sub-domain hosted on the machine where Webmin runs? If not, try using HTTP validation, instead of DNS. I expect, that you have web-server running there, and, to simplify the process of adding new virtual host (domain), use Virtualmin to create new virtual-host, and then request a new certificate using Server Configuration/SSL Certificate/Let’s Encrypt like mentions before.
I have installed webmin/virtualmin through this code:
wget http://software.virtualmin.com/gpl/scripts/install.sh -O /tmp/virtualmin-install.sh
chmod +x /tmp/virtualmin-install.sh
sudo sh /tmp/virtualmin-install.sh
and pic of virtualmin tab is:
++ At this time no virtual server added.
++ just created DNS Master zone in BIND Dns Server and added A Record. and also added the A Record in Domain Registrar for q7.btcloud.eu.**
Okay, read my last two posts, and add virtual server (domain) using Virtualmin, and then request SSL certificate (from Virtualmin tab).
Any update here? 
@Ilia, I have been stucked in dns challenge, if this method failed then I will try using creating virtual server and so on. but right now I have tested using dns challenge and now almost succeeded about to issue lets encrypt wildcard certificate using certbot command is as under:
certbot certonly --manual --preferred-challenges dns --server https://acme-v02.api.letsencrypt.org/directory --manual-public-ip-logging-ok -d ‘*.q7.btcloud.eu’ -d q7.btcloud.eu
I have added one TXT Record in my domain registrar as per dns challenge requirement, and now the result is as under:
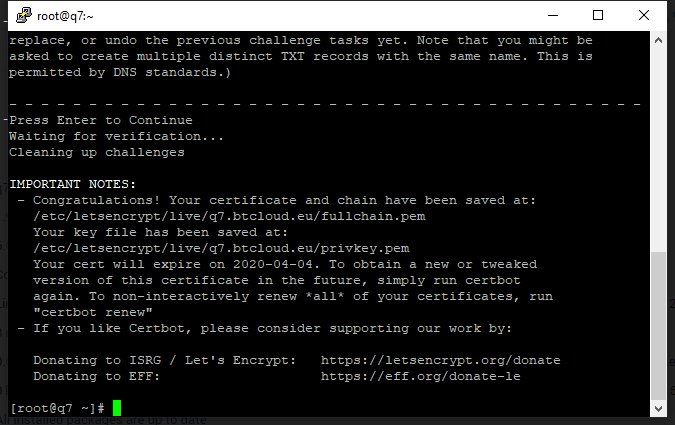
Is that ok, what can I do next?
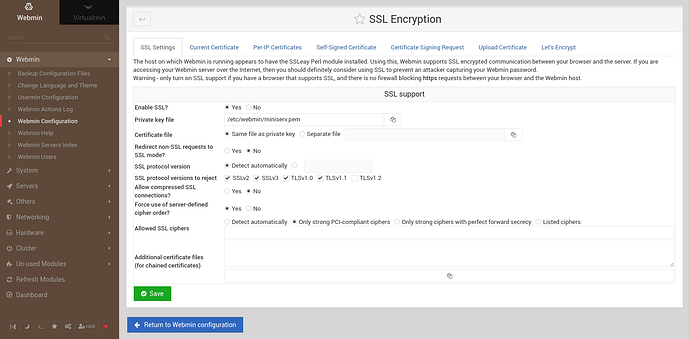
If you have the certificate for your domain, just tell Webmin (miniserv) to use it. You can do it via Webmin/Webmin Confiuration/SSL Encryption page or editing /etc/webmin/config file manually and restarting Webmin. The first method is preferred.
@Ilia, You means the the first method i.e.
Create an virtual host for btcloud.eu and then subserver for q7.btcloud.eu and request for SSL Certificate?
@Ilia, so nice of you, I am really really very thankful to you for your precious advice, Now its really awesome, and I have successfully installed SSL on Webmin Service Host with your help. Webmin is really a great alternate Web Hosting Control Panel. ![]()
Now guide me the next how can I secure Apache, SMPT, POP3, and is the Comodo WAF is good option for mod_security. I have installed on my other server but need your guidance regarding this.
All you need is to use Virtualmin to create a virtual-server (domain) and it will take are of it. Carefully read through the options when creating it and you will be fine.
and is the Comodo WAF is good option
We don’t support it but you can use it if you wish. However, there are simpler options, that are supported on UI side, which is ConfigServer Security and Firewall. It’s very powerful and, as well, has protection against DDoS attacks and many other easily configurable options. It’s easy to install it and set it up.
I have installed on my other server but need your guidance regarding this.
We don’t provided guidance for third-party software configuration. There is a sea of documentations/forums in this regard, and I will leave this to you to investigate on.
We are ready to help but this is outside of the scope of our support. ![]()
You means, If ConfigServer Security & Firewall is installed then there is no need other other WAF. Then its good because I have already installed CSF on this testing server and its working fine.
but after last update of Webmin a new feature came e.g. Bandwidth Monitoring and as ConfigServer Security & Firewall is installed on my server and when I setting up Bandwidth Monitoring then error comes i.e.
Redirecting to /bin/systemctl restart iptables.service
Failed to restart iptables.service: Unit not found.