| SYSTEM INFORMATION | |
|---|---|
| OS type and version | Debian GNU/Linux 11 (bullseye) |
| Virtualmin version | 7.7 |
| Webmin version | 2.021 |
| Usermin version | 1.861 |
Good evening,
as the title suggests, I would like to try to address the problem from another perspective, ie starting from the problem I’m sure of and that is that there are several IPs that are sending spam from my server.
To begin the analysis, I am attaching what I think is the most sensible log, namely the analysis of a queued email, from which various details can be deduced.
It should be noted that the root@luigidonato.it user does not exist.
*** ENVELOPE RECORDS deferred/A/A9526241100 ***
message_size: 4961 839 2 0 4961 0
message_arrival_time: Tue May 9 23:03:11 2023
create_time: Tue May 9 23:03:11 2023
named_attribute: log_ident=A9526241100
named_attribute: rewrite_context=remote
named_attribute: sasl_method=PLAIN
named_attribute: sasl_username=root
sender: root@luigidonato.it
named_attribute: log_client_name=unknown
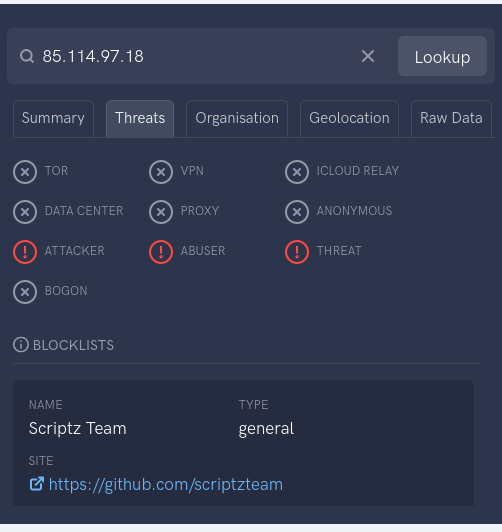
named_attribute: log_client_address=85.114.97.18
named_attribute: log_client_port=46528
named_attribute: log_message_origin=unknown[85.114.97.18]
named_attribute: log_helo_name=[127.0.0.1]
named_attribute: log_protocol_name=ESMTP
named_attribute: client_name=unknown
named_attribute: reverse_client_name=unknown
named_attribute: client_address=85.114.97.18
named_attribute: client_port=46528
named_attribute: server_address=75.119.152.130
named_attribute: server_port=25
named_attribute: helo_name=[127.0.0.1]
named_attribute: protocol_name=ESMTP
named_attribute: client_address_type=2
named_attribute: dsn_orig_rcpt=rfc822;terryfranklin078@gmail.com
original_recipient: terryfranklin078@gmail.com
done_recipient: terryfranklin078@gmail.com
named_attribute: dsn_orig_rcpt=rfc822;a.schmitz-1@web.de
original_recipient: a.schmitz-1@web.de
recipient: a.schmitz-1@web.de
*** MESSAGE CONTENTS deferred/A/A9526241100 ***
Received: from [127.0.0.1] (unknown [85.114.97.18])
by mail.donagest.com (Postfix) with ESMTPA id A9526241100;
Tue, 9 May 2023 23:03:11 +0200 (CEST)
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/simple; d=luigidonato.it;
s=202208; t=1683666192;
bh=rjv8sckOj99DP7+VVrJDCrwifp/hH2xVmFAonbBoJv8=;
h=Date:Subject:From:To:From;
b=acjdHPADKUAPPkx9HHPVdY2WN0b3ejV8PjiB2dcQqw88wrx3khFSvYQYFYh1OPsDN
DbolN/s/nCfKzOBP83ZVxUZHcJIm9uuroh7ScJlXeabp5KI1Tk6cdW1GE467wDVjh0
o0JuCht3wU1njTvRAsQQkBNmJx4I9Ho+VGp96bFMt95VvEY/LDr+1uV864zh/aoKT2
8dCqAJ99KKz1ogLihiFk7pLvtTbMazITREyHYmz4N/d9xhNrjqgSazLZBfwWjRwNuM
bnuu2c+4xZQcCBRfYBi4owutlvJ1xoTaiS7Yr36K+OPWLUY27uJiQ6mOI2e7F/yHee
Wbeg43+sUu3og==
Date: Tue, 9 May 2023 14:03:11 -0700
Subject: Hi teedog New message from CassidyButterBabe
From: root@luigidonato.it
To: terryfranklin078@gmail.com, a.schmitz-1@web.de
MIME-Version: 1.0
Content-Type: multipart/alternative;
boundary=“–_com.android.email_55883954208226”
Message-ID: x4tprlj-injlhs-5B@luigidonato.itThis is a multi-part message in MIME format
----_com.android.email_55883954208226
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: quoted-printableMeet Someone
New Today
Do not be lonely tonight! Dozens of hot ladies want you!
I hope you’re not shybecause I’m DYING to swap sexy pics with you!=
=2E… Just tell me what you want me to take off…https://spamm.er/link
You=E2=80=99re receiving this email because you signed up for o=
ur product newsletter or newsletter of our business partner. If you=E2=
=80=99d like to be removed from our mailing list please click https://spamm.er/link----_com.android.email_55883954208226
Content-Type: text/html; charset=UTF-8
Content-Transfer-Encoding: quoted-printable=20
body{display:flex !important;flex-direction:c= olumn !important;margin:0 !important;} New message from
Meet Someone
New Today
= <span style=3D"font-size:33px; font-style: italic;“>Do not be lonely t=
onight! Dozens of hot ladies want you! <span style=3D"font-style: norm=
al;”>😘
I hope you're not shy ;) because I'm DYING to swap sexy pics with you!= =2E.. Just tell me what you want me to take off....
Send me a private message HERE
Ϗ= 7;
You=E2=80=99re receiving this email because you signed up for= our product newsletter or newsletter of our business partner. If you=E2= =80=99d like to be removed from our mailing list please click here
----_com.android.email_55883954208226–
*** HEADER EXTRACTED deferred/A/A9526241100 ***
*** MESSAGE FILE END deferred/A/A9526241100 ***