| System hostname | redacted.something.cloud (88.88.88.77) | Operating system | Debian Linux 10 |
|---|---|---|---|
| Webmin version | 2.021 | Usermin version | 1.861 |
| Virtualmin version | 7.7 | Authentic theme version | 20.21 |
I would try all the below mentioned questions myself but I don’t want to lock myself out, thank you for understanding ![]()
Ok, I’m posting this after having done my own research but don’t feel like I found a satisfying answer myself. I employed ChatGPT as well but it seems to provide information that is outdated or just wrong…
Anyway, here is my situation:
I have a small webserver in the cloud. Access to it is restricted and only allowed for one specific IP address and SSH PKI + Passphrase.
On it, I installed Virtualmin and set up a virtual server redacted.something.cloud - I set up 2FA on it. I’m trying to achive the following outcome:
The root-admin-webmin-panel should not be accessible from anywhere on the internet. So to achive this, according to my current knowledge, I could go two ways:
I’m not 100% sure what the difference between those two options is. I have a Dyndns-service for my home network, so if I put in mydyndns.com in the allowed IP address, I should be able to login from only when I’m connected to my home network, right?
On the other hand, if I Bind to IP address in Listen on IPs and ports, I could do the same + specify the port. I have read on the wiki about these two and it says: “Webmin usually listens for connections on port 10000 on all of your system’s IP addresses.”
OK, so if I have multiple virtual servers
redacted1.something.cloud
redacted2.something.cloud
redacted3.something.cloud
admn.something.cloud
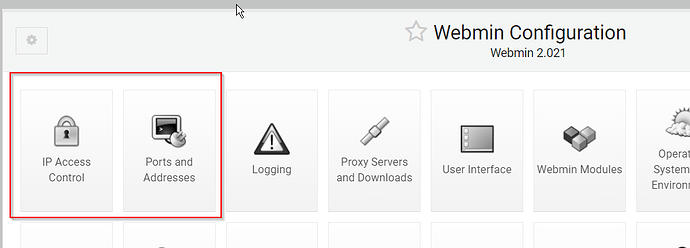
By setting up IP Access control and specifying Ports and Addresses, I could achieve my desired outcome:
Access Webmin Admin panel only from IP Address 91.54.10.10 by typing in the browser https://admn.something.cloud:989
Ok, so I also found this option that is kind of obvious and I feel a bit stupid for not having seen it so far: Under VirtualMin → Edit Virtual Servers, I have disabled the apache server for the admn.something.cloud and disabled the virtualmin login for the other subdomains. But it still doesn’t work on the root account, I can still see the login page for the non-admin domains with the right port.