Joe
July 1, 2024, 9:34pm
1
Howdy all,
This is not really Virtualmin news, but it probably effects most of you. There has been a vulnerability discovered in most recent and some very old versions of openssh-server. It is a privileged RCE, so pretty much as dangerous as a vulnerability can be. It effects the version of OpenSSH Server found in most of the current Linux distros supported by Virtualmin. Updates are available for all of the currently maintained distros, as far as I can tell.
Anyway, if you’ve got one of the impacted OpenSSH Server versions, you need to update! Immediately, if not sooner!
2 Likes
xorax
July 1, 2024, 10:49pm
2
Following Debian security tracker and the introducer commit it should affect only the openssh server version >= 8.5 p1 , so only Debian 12 is affected (Debian 11 Bullseye and older use v8.4 max )
Am I right ?
Thanks !!!
1 Like
Joe
July 1, 2024, 10:57pm
3
Yep, that sounds right to me, now that I’ve spent some time looking at versions that came with various distros.
Looks like CentOS 8 and 7 are also probably fine. And, updates are available for Rocky/Alma/RHEL 9.
I’ll update the post, as I think it’s less alarming than I initially feared.
2 Likes
ID10T
July 2, 2024, 12:10am
4
When @xorax said Debian 12 but not prior I was wondering if it was this but it has a different CVE… Damned this is getting worrisome.
Clever hack but I guess it was a performance killer so was probably gonna get weeded out.
Mainly posting as a point of interest.
Steini
July 10, 2024, 9:42am
5
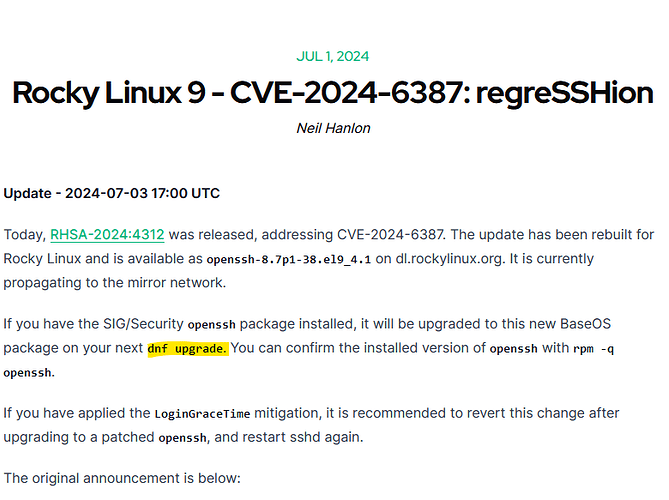
A new vulnerability emerged and affects sshd that ships with RHEL9: NVD - CVE-2024-6409
sshd server shipped with Red Hat Enterprise Linux 9, while upstream versions of sshd are not impact by this flaw.
Is upstream = Rocky? Hope so.
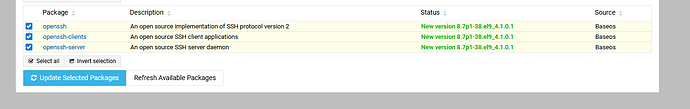
Just ran refresh packages, hopefully its the patch
P.S.
1 Like
verne
July 11, 2024, 2:30am
7
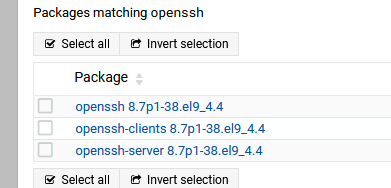
as a licensed RedHat shop, I took a quick peek … I downloaded openssh-8.7p1-38.el9_4.4.x86_64.rpm and looked at the ChangeLog:
rpm -q --changelog -p openssh-8.7p1-38.el9_4.4.x86_64.rpm | more
* Wed Jul 03 2024 Dmitry Belyavskiy <dbelyavs@redhat.com> - 8.7p1-38.4
- rebuilt
* Wed Jul 03 2024 Dmitry Belyavskiy <dbelyavs@redhat.com> - 8.7p1-38.3
- rebuilt
* Mon Jul 01 2024 Dmitry Belyavskiy <dbelyavs@redhat.com> - 8.7p1-38.2
- Possible remote code execution due to a race condition (CVE-2024-6409)
Resolves: RHEL-45740
* Fri Jun 28 2024 Dmitry Belyavskiy <dbelyavs@redhat.com> - 8.7p1-38.1
- Possible remote code execution due to a race condition (CVE-2024-6387)
Resolves: RHEL-45347
so … RedHat has addressed CVE-2024-6409 … time for everyone to update openssh !!
the post above by @stefan1959 seems to show Rocky already has it
1 Like
There was another update today. Just refresh your packages.
No, for rocky there’s separate channel for security and you need to downgrade to get the patched version of that. More info here .
dnf install rocky-security-release -y
dnf config-manager --enable security-common
yum install openssh-8.7p1-38.el9_4.security.0.5.x86_64
echo "exclude=openssh openssh-clients openssh-server" >> /etc/yum.conf
1 Like
@xorax ,
SSH “1:9.2p1-2+deb12u3” introduced a fix, which is what Debian 12 users should be using if they keep their system updated.
I think that’s updated and going out using dnf upgrade or am I reading that wrong
what I have
Sorry my bad didn’t read throrough, they confirmed it contain the patch on their forum
system
July 24, 2024, 11:54pm
13
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.