Are there any plans to enable Virtualmin to manage Lets Encrypt certificates using DNS-01 Challenge on external DNS servers?
The short answer is no.
The long answer is, when requesting a certificate using DNS-01 you are required to add a random dns record to your dns (this changes with every request for a certificate) which if the dns is virtualmin managed this is achievable, but third party dns servers require you to log into their interface to add/update records, which is not practicable to do.
Virtualmin Pro supports DNS validation for any DNS services it supports. (Route 53, Google DNS, and maybe Cloudflare, I think?)
It also works with Cloudmin Services managed DNS.
The short answer is yes, if Virtualmin is managing your DNS externally.
Wildcard is dns challenge, I will have a play.
P.S. Is it this record?
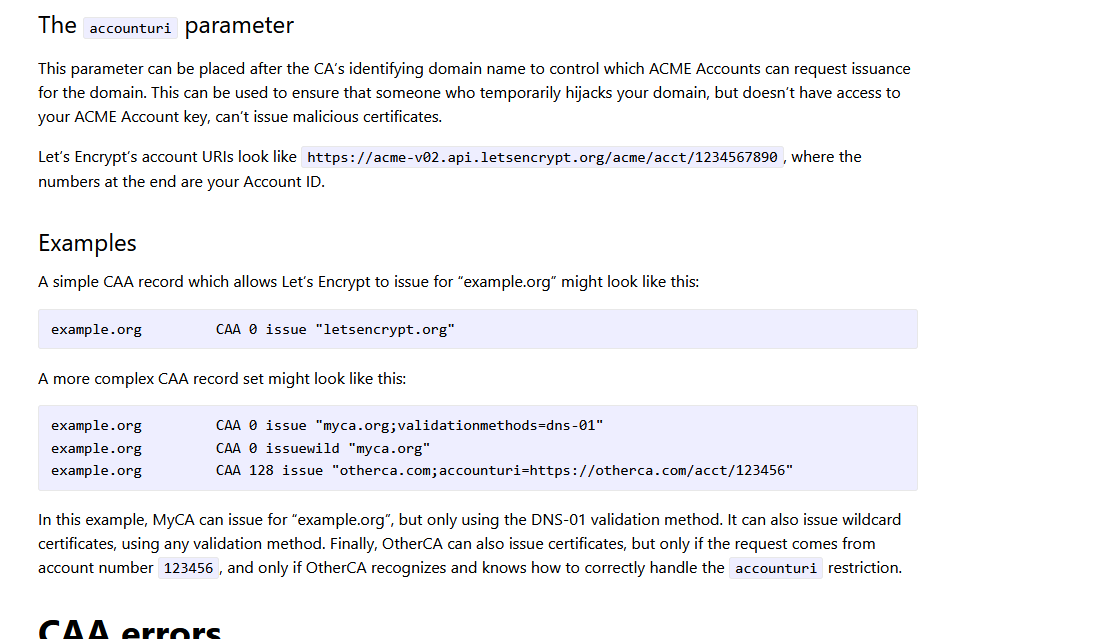
CAA - Certificate Authority 0 issuewild letsencrypt.org
No, that’s wildcards, which must validate with DNS. Most folks don’t need a wildcard and most folks don’t benefit from a wildcard, and wildcards have security implications.
If Virtualmin is managing your DNS, it will automatically validate via DNS if web validation fails. It is not an option you choose. It just does the thing.
Wildcard certs are unrelated to your question. Wildcards must be validated via DNS, but that has nothing to do with getting a regular cert. For regular certs, Virtualmin will try both, if both are available (i.e. if you have a website and if Virtualmin is managing DNS). If web fails, DNS will be attempted.
Ok, so leave this record will work as a fallback?
Maybe not, seeing there is a issuewild there.
If you’re having a problem with web validation that means you need to use DNS validation, maybe you should tell us about that problem. I’m having a hard time coming up with a scenario where DNS validation is preferable to web validation.
I have 2 domains that are mail only, so I had to turn on web services to get certificates for the mail. I guess OP is blue skying the option.
I think going on the docs
example.org CAA 0 issue "letsencrypt.org"
Would do the job
I don’t know. OP hasn’t told us what they’re trying to do.
But, the short answer is Virtualmin already supports DNS Let’s Encrypt validation on local or remote DNS servers, as long as Virtualmin is managing DNS.
Good to know, I always thought dns would fail. With external that record should allow as well?
I will add and test on those mail only accounts.
P.S. no good, like you say the dns needs to be internal.
It started because I have a couple of email only domains where the websites are hosted elsewhere - usually the web developer.
At present I edit DNS to point the web here, manually request an LE certificate, then switch the DNS back.
Then I have a large web blocklist to stop junk/hackers at the gateway. but as LE get more random servers, some of those are blocked making it hit and miss each renewal request.
Then I have 2 remote servers that don’t do web, so I block port 80 (and everything else they don’t need) at the master VPS firewall, and have to open it to renew LE certs.
So this seems a simple solution for all these problems.
I tested it manually, and it works - also much faster than http renewal, but all my DNS is on separate servers and VMin doesn’t manage it.
A while ago I did setup a spare VMin and webmin servers to test using it as master/slave, it’s obviously a system that works, I don’t recall why I stopped apart from a few urgent issue came along.
I read it wouldn’t work without VMin being in control, hence I asked mainly to see if it is possible for VMin to handle a DNS request without it being in charge of the DNS.
It does not need to be hosted locally. Virtualmin can manage remote DNS in a variety of ways. Virtualmin must be managing DNS for DNS validation to work. It does not have to be local.
Virtualmin cannot perform DNS validation if Virtualmin is not managing DNS. I don’t know how it possibly could. It needs to be able to create records for DNS validation to work. Virtualmin can manage DNS on separate servers (or cloud services) in a variety of ways.
But, certbot is the best option for your case, I think. There are many plugins for certbot to allow it to work with a variety of DNS systems and APIs.
For future reference, please say what you’re actually trying to do and why it’s failing rather than making us all dance around the actual problem. This whole thread has been about the wrong question; it’s the question you asked, but not the question you actually wanted answered.
When changing a website’s server, I want to install the SSL certificate on the destination server beforehand.
This is to avoid the site becoming inaccessible while waiting for the SSL certificate to be issued.
Even if the site is viewable via HTTP, access will still come via HTTPS, so redirecting to HTTP is not possible.
To avoid this, I need to use DNS-01 verification to install the SSL certificate on the destination server before changing the DNS A record.
For the renewal three months later, I believe the current procedure—first attempting HTTP-01 authentication and switching to DNS-01 if it fails—should be fine.
This is because the website will already be migrated, so HTTP-01 verification should succeed.
However, this method won’t work in Randomz’s case (where an SSL certificate is needed for email, and the mail server and web server are separate).
You could copy the old certificate from the old server during migration. Then when the switch is flipped, request a new one.
It’s also possible to proxy .well-known to the new server. But, probably easiest to just copy the existing cert.