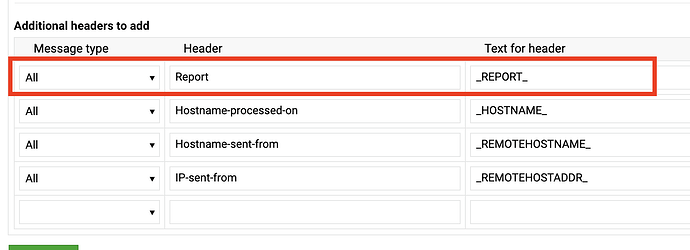
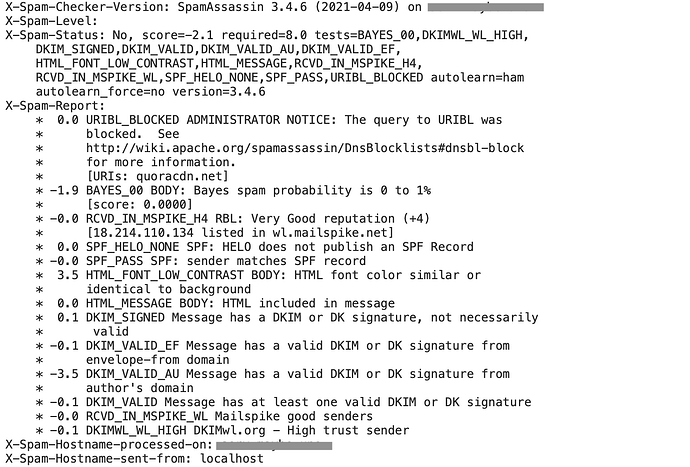
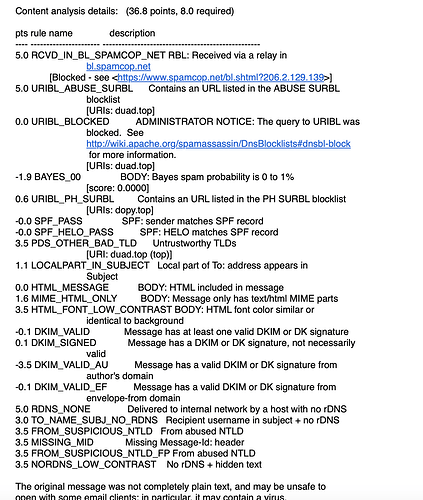
I was checking.
There’s a lot more here.
I generated a file that I moved to the PC to check better.
This is for email spam
Apr 28 21:59:52 MY-SRV postfix/anvil[159170]: statistics: max connection rate 1/60s for (smtp:172.116.51.241) at Apr 28 21:55:02
Apr 28 21:59:52 MY-SRV postfix/anvil[159170]: statistics: max connection count 1 for (smtp:172.116.51.241) at Apr 28 21:55:02
Apr 28 21:59:52 MY-SRV postfix/anvil[159170]: statistics: max cache size 2 at Apr 28 21:55:10
Apr 28 22:15:07 MY-SRV postfix/pickup[158326]: AAE2517CEACD: uid=1007 from=<evoke@earnmorenow.info>
Apr 28 22:15:07 MY-SRV postfix/cleanup[165495]: AAE2517CEACD: message-id=<B3Jllr1bhuEf7nG7EuxeRXceV0qKHKtWBcAx7H8oSw4@MY-DOMAIN>
Apr 28 22:15:07 MY-SRV postfix/qmgr[1772]: AAE2517CEACD: from=<evoke@earnmorenow.info>, size=3131, nrcpt=2 (queue active)
Apr 28 22:15:08 MY-SRV postfix/local[165498]: AAE2517CEACD: to=<"MY-MAILBOX@MY-DOMAIN"@MY-SRV>, orig_to=<MY-MAILBOX@MY-DOMAIN>, relay=local, delay=0.71, delays=0.02/0/0/0.68, dsn=2.0.0, status=sent (delivered to command: /usr/bin/procmail-wrapper -o -a $DOMAIN -d $LOGNAME)
Apr 28 22:15:09 MY-SRV postfix/smtp[165497]: AAE2517CEACD: to=<evoke@earnmorenow.info>, relay=inbound-smtp.us-west-2.amazonaws.com[52.43.162.244]:25, delay=2.1, delays=0.02/0.01/1.5/0.65, dsn=2.0.0, status=sent (250 OK n3ihbff63ue572mo7s46793uogipcftcccgr5301)
Apr 28 22:15:09 MY-SRV postfix/qmgr[1772]: AAE2517CEACD: removed
Apr 28 22:23:13 MY-SRV postfix/smtpd[166260]: warning: hostname waffles.scanf.shodan.io does not resolve to address 164.92.114.247
Apr 28 22:23:13 MY-SRV postfix/smtpd[166260]: connect from unknown[164.92.114.247]
Apr 28 22:23:18 MY-SRV postfix/smtpd[166265]: warning: hostname waffles.scanf.shodan.io does not resolve to address 164.92.114.247
Apr 28 22:23:18 MY-SRV postfix/smtpd[166265]: connect from unknown[164.92.114.247]
Apr 28 22:23:18 MY-SRV postfix/smtpd[166265]: warning: TLS library problem: error:0A0000F5:SSL routines::unexpected record:../ssl/record/rec_layer_s3.c:1742:
Apr 28 22:23:18 MY-SRV postfix/smtpd[166265]: lost connection after CONNECT from unknown[164.92.114.247]
Apr 28 22:23:18 MY-SRV postfix/smtpd[166265]: disconnect from unknown[164.92.114.247] commands=0/0
Apr 28 22:23:21 MY-SRV postfix/smtpd[166265]: warning: hostname waffles.scanf.shodan.io does not resolve to address 164.92.114.247
Meanwhile I see that there are frequent foreign accesses.
I hope they are blocked by Fail2ban or something else.
Apr 27 11:43:28 MY-SRV postfix/smtpd[449836]: connect from unknown[196.0.107.190]
Apr 27 11:43:35 MY-SRV postfix/smtpd[449839]: connect from unknown[221.163.227.238]
Apr 27 11:43:37 MY-SRV postfix/smtpd[449839]: lost connection after CONNECT from unknown[221.163.227.238]
Apr 27 11:43:37 MY-SRV postfix/smtpd[449839]: disconnect from unknown[221.163.227.238] commands=0/0
Apr 27 11:43:38 MY-SRV postfix/smtpd[449836]: warning: unknown[196.0.107.190]: SASL LOGIN authentication failed: authentication failure, sasl_username=anabell
Apr 27 11:43:41 MY-SRV postfix/smtpd[449836]: lost connection after AUTH from unknown[196.0.107.190]
Apr 27 11:43:41 MY-SRV postfix/smtpd[449836]: disconnect from unknown[196.0.107.190] ehlo=1 auth=0/1 commands=1/2
Apr 29 05:33:02 MY-SRV postfix/smtpd[273585]: connect from unknown[unknown]
Apr 29 05:33:02 MY-SRV postfix/smtpd[273585]: SSL_accept error from unknown[unknown]: Connection reset by peer
Apr 29 05:33:02 MY-SRV postfix/smtpd[273585]: lost connection after CONNECT from unknown[unknown]
Apr 29 05:33:02 MY-SRV postfix/smtpd[273585]: disconnect from unknown[unknown] commands=0/0
Apr 29 05:33:33 MY-SRV postfix/smtpd[273585]: warning: hostname donut.scanf.shodan.io does not resolve to address 64.226.86.7
A
Attempts also with real users’ boxes
Apr 29 05:10:09 MY-SRV postfix/smtpd[263502]: connect from unknown[94.156.8.201]
Apr 29 05:10:11 MY-SRV postfix/smtpd[263502]: warning: unknown[94.156.8.201]: SASL LOGIN authentication failed: authentication failure, sasl_username=My-MAILBOX@MY-DOMAIN
Apr 29 05:10:11 MY-SRV postfix/smtpd[263502]: disconnect from unknown[94.156.8.201] ehlo=2 starttls=1 auth=0/1 quit=1 commands=4/5
I also see
Apr 29 02:00:18 MY-SRV postfix/smtpd[218705]: connect from unknown[159.89.124.112]
Apr 29 02:00:18 MY-SRV postfix/smtpd[218705]: improper command pipelining after CONNECT from unknown[159.89.124.112]: \026\003\001\001E\001\000\001A\003\003\322-X6\rVQ\373U=1|e\236\245x\322\200\355\350\231U\220\314;G\334\273\302\211\312, W\324-\315\266V%\267\270\206\357\300&\v^\177\230\240\005\222\302\300\t\330\300\334\v\330G\332)\301\000>\023\002\023\003\023\001\300,\3000\000\237\314\251\314\250\314\252\300+\300/
Apr 29 02:00:18 MY-SRV postfix/smtpd[218705]: lost connection after CONNECT from unknown[159.89.124.112]
Apr 29 02:00:18 MY-SRV postfix/smtpd[218705]: disconnect from unknown[159.89.124.112] commands=0/0
Apr 29 00:26:49 MY-SRV postfix/smtpd[196650]: connect from unknown[193.86.95.34]
Apr 29 00:26:49 MY-SRV postfix/smtpd[196650]: improper command pipelining after CONNECT from unknown[193.86.95.34]: {"id":1,"jsonrpc":"2.0","method":"login","params":{"login":"49CYQrmrqP2LyHQdMY26JGiq3M9cxFkiSU9PyfSE
Apr 29 00:26:49 MY-SRV postfix/smtpd[196650]: warning: non-SMTP command from unknown[193.86.95.34]: {"id":1,"jsonrpc":"2.0","method":"login","params":{"login":"49CYQrmrqP2LyHQdMY26JGiq3M9cxFkiSU9PyfSE
Apr 29 00:26:49 MY-SRV postfix/smtpd[196650]: disconnect from unknown[193.86.95.34] unknown=0/1 commands=0/1