Ubuntu Server 22.04.4 | Webmin 2.202 | Usermin 2.102 | Virtualmin 7.20.2 | Theme 21.20.7 | Perl 5.034000 | Apache 2.4.52 | Python 3.10.12 | BIND 9.18 | MariaDB 10.6.18 | PHP 8.3.11 | Postfix 3.6.4 | Dovecot 2.3.16 | SpamAssassin 3.4.6 | CSF 14.21 | ClamAV 0.103.11 | OpenSSH 8.9 | OpenSSL 3.0.2 | Certbot 1.21.0 | Logrotate 3.19.0 | NTP 1:4.2.8p15 | Lynis 3.1.1
Package updates [All installed packages are up to date]
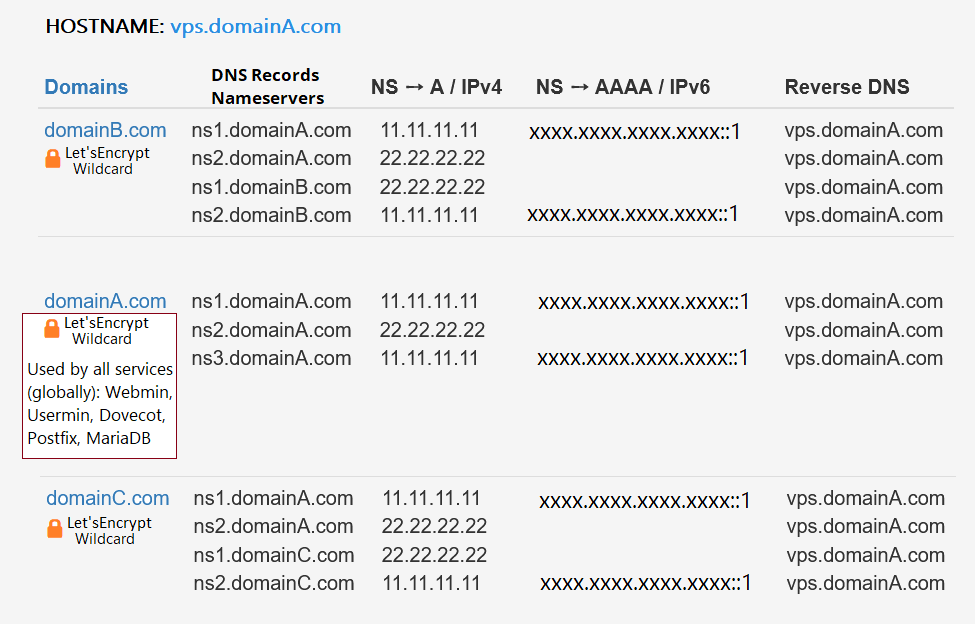
Name-based Virtual Hosts share 3 IP addresses (2x IPv4 + 1x IPV6)
The domains and the server have passed all the following tests with absolute success.
hstspreload.org, intodns.com, dnsviz.net, dnssec-analyzer.verisignlabs.com
zonemaster.net, en.internet.nl, www.mail-tester.com, www.hardenize.com
www.mailhardener.com/tools/, easydmarc.com/tools/, www.ssllabs.com
All registry entries (dns records) work flawlessly for all services. Mail, Databases, Firewall, Anti-Spam, Wordpress, SSH, etc. The communication of the server with the outside world works seamlessly, without any error anywhere.
mta-sts, mx, spf, dmarc, dkim, bimi, tlsa, dnssec, dane, rdns
I try to enable DNSOverTLS=yes option in resolved.conf document but every time after restarting systemd-resolved.service curl, dig, delv don’t bring results to terminal queries…
I also tried DNSOverTLS=opportunistic but again to no avail.
Tried enabling DNS=ip_address#hostname as well but no luck with that either.
Could the problem be that the DNS of my server works on a Name-based basis because I have to divide the IPs into 3 domains and all the rdns look at the hostname?
Does anyone know how to enable DNSOverTLS?