| SYSTEM INFORMATION | |
|---|---|
| OS type and version | Debian 12 |
| Webmin version | 2.111 and virtualmin 7.10.0 |
Hello
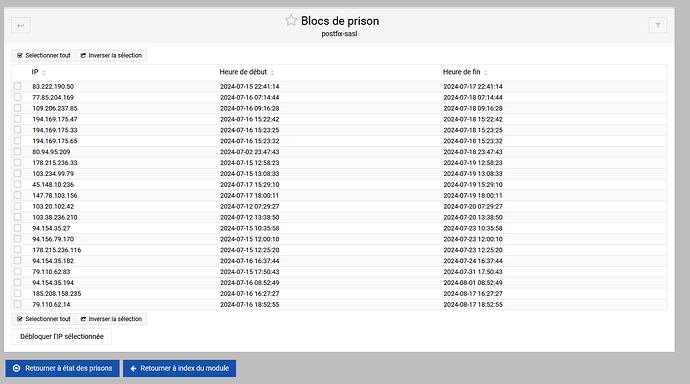
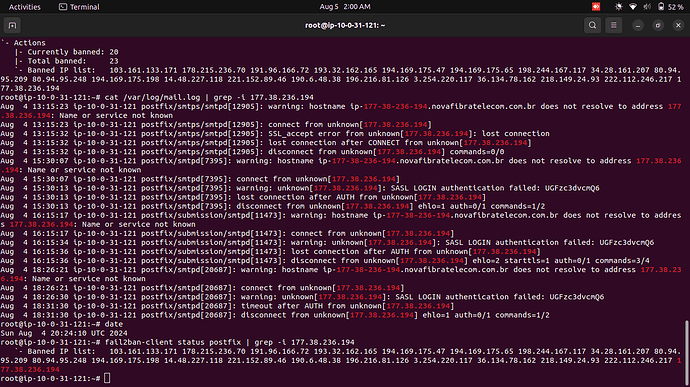
Since December 2023, I have a new Debian 12 server with Virtualmin/Webmin. Before December 2023 and since 2010, I had CentOS with cPanel/WHM. I have a problem with Fail2ban; it doesn’t ban any attacks on Postfix SASL.
Jun 15 20:38:38 ns postfix/smtpd[4151380]: connect from unknown[80.244.11.65]
Jun 15 20:38:38 ns postfix/smtpd[4151372]: connect from unknown[80.244.11.67]
Jun 15 20:38:38 ns postfix/smtpd[4151376]: connect from unknown[80.244.11.147]
Jun 15 20:38:38 ns postfix/smtpd[4151386]: disconnect from unknown[80.244.11.121] quit=1 commands=1
Jun 15 20:38:38 ns postfix/smtpd[4151386]: connect from unknown[80.244.11.120]
Jun 15 20:38:40 ns postfix/smtpd[4151379]: warning: unknown[80.244.11.66]: SASL LOGIN authentication failed: authentication failure, sasl_username=carolyn
Jun 15 20:38:40 ns postfix/smtpd[4151413]: warning: unknown[80.244.11.146]: SASL LOGIN authentication failed: authentication failure, sasl_username=oa
Jun 15 20:38:40 ns postfix/smtpd[4151387]: warning: unknown[80.244.11.121]: SASL LOGIN authentication failed: authentication failure, sasl_username=deka
Jun 15 20:38:40 ns postfix/smtpd[4151388]: warning: unknown[80.244.11.120]: SASL LOGIN authentication failed: authentication failure, sasl_username=new3
Jun 15 20:38:40 ns postfix/smtpd[4151384]: warning: unknown[80.244.11.148]: SASL LOGIN authentication failed: authentication failure, sasl_username=mscan
Jun 15 20:38:40 ns postfix/smtpd[4151388]: too many errors after AUTH from unknown[80.244.11.120]
Jun 15 20:38:40 ns postfix/smtpd[4151388]: disconnect from unknown[80.244.11.120] ehlo=1 auth=0/1 rset=1 commands=2/3
Jun 15 20:38:40 ns postfix/smtpd[4151387]: too many errors after AUTH from unknown[80.244.11.121]
Jun 15 20:38:40 ns postfix/smtpd[4151379]: too many errors after AUTH from unknown[80.244.11.66]
Jun 15 20:38:40 ns postfix/smtpd[4151384]: too many errors after AUTH from unknown[80.244.11.148]
Jun 15 20:38:40 ns postfix/smtpd[4151387]: disconnect from unknown[80.244.11.121] ehlo=1 auth=0/1 rset=1 commands=2/3
Jun 15 20:38:40 ns postfix/smtpd[4151379]: disconnect from unknown[80.244.11.66] ehlo=1 auth=0/1 rset=1 commands=2/3
Jun 15 20:38:40 ns postfix/smtpd[4151384]: disconnect from unknown[80.244.11.148] ehlo=1 auth=0/1 rset=1 commands=2/3
Jun 15 20:38:40 ns postfix/smtpd[4151388]: connect from unknown[80.244.11.146]
Jun 15 20:38:40 ns postfix/smtpd[4151379]: connect from unknown[80.244.11.148]
Jun 15 20:38:40 ns postfix/smtpd[4151387]: connect from unknown[80.244.11.65]
Jun 15 20:38:40 ns postfix/smtpd[4151384]: connect from unknown[80.244.11.147]
Jun 15 20:38:40 ns postfix/smtpd[4151413]: too many errors after AUTH from unknown[80.244.11.146]
Jun 15 20:38:40 ns postfix/smtpd[4151413]: disconnect from unknown[80.244.11.146] ehlo=1 auth=0/1 rset=1 commands=2/3
Jun 15 20:38:40 ns postfix/smtpd[4151413]: connect from unknown[80.244.11.69]
Jun 15 20:38:42 ns postfix/smtpd[4151398]: warning: unknown[80.244.11.120]: SASL LOGIN authentication failed: authentication failure, sasl_username=new3
Jun 15 20:38:42 ns postfix/smtpd[4151401]: warning: unknown[80.244.11.69]: SASL LOGIN authentication failed: authentication failure, sasl_username=mission
Jun 15 20:38:42 ns postfix/smtpd[4151397]: warning: unknown[80.244.11.140]: SASL LOGIN authentication failed: authentication failure, sasl_username=mssql
Jun 15 20:38:42 ns postfix/smtpd[4151399]: warning: unknown[80.244.11.120]: SASL LOGIN authentication failed: authentication failure, sasl_username=new3
Jun 15 20:38:42 ns postfix/smtpd[4151398]: too many errors after AUTH from unknown[80.244.11.120]
Jun 15 20:38:42 ns postfix/smtpd[4151399]: too many errors after AUTH from unknown[80.244.11.120]
Jun 15 20:38:42 ns postfix/smtpd[4151397]: too many errors after AUTH from unknown[80.244.11.140]
Jun 15 20:38:42 ns postfix/smtpd[4151398]: disconnect from unknown[80.244.11.120] ehlo=1 auth=0/1 rset=1 commands=2/3
Jun 15 20:38:42 ns postfix/smtpd[4151397]: disconnect from unknown[80.244.11.140] ehlo=1 auth=0/1 rset=1 commands=2/3
Jun 15 20:38:42 ns postfix/smtpd[4151399]: disconnect from unknown[80.244.11.120] ehlo=1 auth=0/1 rset=1 commands=2/3
Jun 15 20:38:42 ns postfix/smtpd[4151400]: warning: unknown[80.244.11.148]: SASL LOGIN authentication failed: authentication failure, sasl_username=mscan
Jun 15 20:38:42 ns postfix/smtpd[4151401]: too many errors after AUTH from unknown[80.244.11.69]
Jun 15 20:38:42 ns postfix/smtpd[4151401]: disconnect from unknown[80.244.11.69] ehlo=1 auth=0/1 rset=1 commands=2/3
Jun 15 20:38:42 ns postfix/smtpd[4151400]: too many errors after AUTH from unknown[80.244.11.148]
Jun 15 20:38:42 ns postfix/smtpd[4151400]: disconnect from unknown[80.244.11.148] ehlo=1 auth=0/1 rset=1 commands=2/3
Jun 15 20:38:42 ns postfix/smtpd[4151399]: connect from unknown[80.244.11.121]
Jun 15 20:38:42 ns postfix/smtpd[4151398]: connect from unknown[80.244.11.69]
Jun 15 20:38:42 ns postfix/smtpd[4151397]: connect from unknown[80.244.11.140]
Jun 15 20:38:42 ns postfix/smtpd[4151397]: improper command pipelining after CONNECT from unknown[80.244.11.140]: QUIT\r\n
Jun 15 20:38:42 ns postfix/smtpd[4151401]: connect from unknown[80.244.11.65]
Jun 15 20:38:42 ns postfix/smtpd[4151400]: connect from unknown[80.244.11.120]
Jun 15 20:38:42 ns postfix/smtpd[4151397]: disconnect from unknown[80.244.11.140] quit=1 commands=1
Jun 15 20:38:42 ns postfix/smtpd[4151397]: connect from unknown[80.244.11.120]
Is there a complete method that works in 2024?
I have spent 6 hours researching and testing various solutions provided by ChatGPT and Gemini, but nothing works; no IP addresses are automatically blacklisted.
It’s quite frustrating because the mail server lags a lot and takes a long time to send emails. I can’t manually filter the IPs because new ones keep coming back a few days later. For your information, firewalld is my firewall.
Thank you in advance.
Best regards.