Hello,
fail2ban is not working properly with sshd. I have tried bannning the attackers with iptables-allports, iptables-multiport and route. None of them worked.
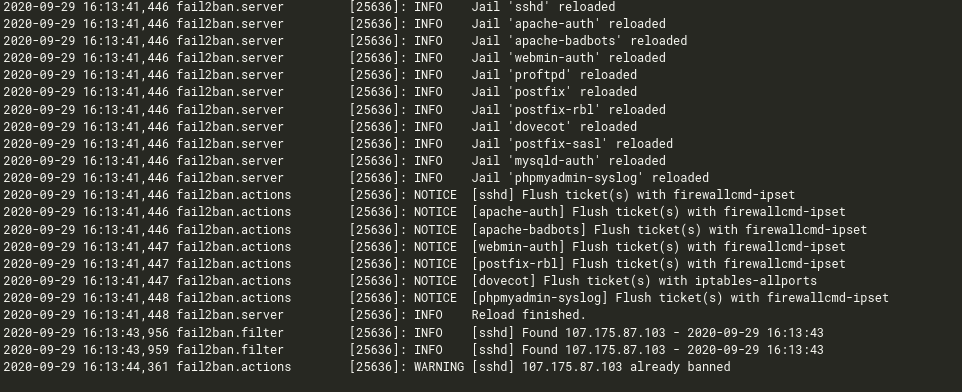
With all of them I see the attacks continue:
2020-09-24 10:19:48,005 fail2ban.filter [25636]: INFO [sshd] Found 139.9.122.153 - 2020-09-24 10:19:48
2020-09-24 10:20:02,220 fail2ban.filter [25636]: INFO [sshd] Found 120.78.160.213 - 2020-09-24 10:20:02
2020-09-24 10:20:02,222 fail2ban.filter [25636]: INFO [sshd] Found 120.78.160.213 - 2020-09-24 10:20:02
2020-09-24 10:20:02,991 fail2ban.actions [25636]: WARNING [sshd] 120.78.160.213 already banned
2020-09-24 10:20:04,074 fail2ban.filter [25636]: INFO [sshd] Found 120.78.160.213 - 2020-09-24 10:20:04
2020-09-24 10:20:24,907 fail2ban.filter [25636]: INFO [sshd] Found 139.9.122.153 - 2020-09-24 10:20:24
2020-09-24 10:20:24,907 fail2ban.filter [25636]: INFO [sshd] Found 139.9.122.153 - 2020-09-24 10:20:24
2020-09-24 10:20:25,018 fail2ban.actions [25636]: WARNING [sshd] 139.9.122.153 already banned
besides with route I get the following errors:
2020-09-22 13:15:04,914 fail2ban.utils [25636]: Level 39 7fc716191348 -- exec: ip route del unreachable 222.186.10.49
2020-09-22 13:15:04,914 fail2ban.utils [25636]: ERROR 7fc716191348 -- stderr: 'RTNETLINK answers: No such process'
2020-09-22 13:15:04,914 fail2ban.utils [25636]: ERROR 7fc716191348 -- returned 2
2020-09-22 13:15:04,915 fail2ban.actions [25636]: ERROR Failed to execute unban jail 'sshd' action 'route' info 'ActionInfo({'ip': '222.186.10.49', 'family': 'inet4', 'ip-rev': '49.10.186.222.', 'ip-host': None, 'fid': '222.186.10.49', 'failures': 5, 'time': 1600764278.0, 'matches': 'Sep 22 10:43:58 anton sshd[4833]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 10:44:00 anton sshd[4833]: Failed password for invalid user ts from 222.186.10.49 port 30586 ssh2\nSep 22 10:44:38 anton sshd[5611]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 ', 'restored': 0, 'F-*': {'matches': ['Sep 22 10:43:58 anton sshd[4833]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 ', 'Sep 22 10:44:00 anton sshd[4833]: Failed password for invalid user ts from 222.186.10.49 port 30586 ssh2', 'Sep 22 10:44:38 anton sshd[5611]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 '], 'failures': 5, 'mlfid': ' anton sshd[4833]: ', 'user': 'ts', 'ip4': '222.186.10.49'}, 'ipmatches': 'Sep 22 12:02:14 anton sshd[18758]: Failed password for root from 222.186.10.49 port 59300 ssh2\nSep 22 12:02:54 anton sshd[18770]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:02:56 anton sshd[18770]: Failed password for invalid user gd from 222.186.10.49 port 65358 ssh2\nSep 22 12:03:34 anton sshd[18785]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:03:35 anton sshd[18785]: Failed password for invalid user ralf from 222.186.10.49 port 6908 ssh2\nSep 22 12:04:13 anton sshd[19604]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:04:15 anton sshd[19604]: Failed password for invalid user internet1 from 222.186.10.49 port 12962 ssh2\nSep 22 12:04:59 anton sshd[19628]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:05:02 anton sshd[19628]: Failed password for invalid user testftp from 222.186.10.49 port 19018 ssh2\nSep 22 12:05:37 anton sshd[19670]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:05:39 anton sshd[19670]: Failed password for invalid user fax from 222.186.10.49 port 25076 ssh2\nSep 22 12:06:14 anton sshd[19679]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:06:15 anton sshd[19679]: Failed password for invalid user test from 222.186.10.49 port 31134 ssh2\nSep 22 12:06:57 anton sshd[19691]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:06:59 anton sshd[19691]: Failed password for invalid user simedw from 222.186.10.49 port 37194 ssh2\nSep 22 12:07:37 anton sshd[19702]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:07:39 anton sshd[19702]: Failed password for invalid user linda from 222.186.10.49 port 43250 ssh2\nSep 22 12:08:18 anton sshd[19712]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:08:21 anton sshd[19712]: Failed password for invalid user samba from 222.186.10.49 port 49304 ssh2\nSep 22 12:09:00 anton sshd[19720]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:09:02 anton sshd[19720]: Failed password for invalid user heinrich from 222.186.10.49 port 55344 ssh2\nSep 22 12:09:39 anton sshd[20550]: Failed password for root from 222.186.10.49 port 61404 ssh2\nSep 22 12:10:21 anton sshd[20603]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:10:23 anton sshd[20603]: Failed password for invalid user arao from 222.186.10.49 port 2952 ssh2\nSep 22 12:10:59 anton sshd[20613]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:11:01 anton sshd[20613]: Failed password for invalid user upload from 222.186.10.49 port 9008 ssh2\nSep 22 12:11:40 anton sshd[20621]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:11:42 anton sshd[20621]: Failed password for invalid user master from 222.186.10.49 port 15066 ssh2\nSep 22 12:12:24 anton sshd[20631]: Failed password for irc from 222.186.10.49 port 21132 ssh2\nSep 22 12:13:06 anton sshd[20642]: Failed password for root from 222.186.10.49 port 27192 ssh2\nSep 22 12:13:45 anton sshd[20650]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:13:47 anton sshd[20650]: Failed password for invalid user amavis from 222.186.10.49 port 33250 ssh2\nSep 22 12:14:23 anton sshd[21417]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:14:25 anton sshd[21417]: Failed password for invalid user test from 222.186.10.49 port 39312 ssh2\nSep 22 12:15:05 anton sshd[21461]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:15:07 anton sshd[21461]: Failed password for invalid user fernandez from 222.186.10.49 port 45368 ssh2\nSep 22 12:15:47 anton sshd[21470]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:15:49 anton sshd[21470]: Failed password for invalid user wwwadmin from 222.186.10.49 port 51424 ssh2\nSep 22 12:16:27 anton sshd[21493]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:16:29 anton sshd[21493]: Failed password for invalid user abc from 222.186.10.49 port 57474 ssh2\nSep 22 12:17:08 anton sshd[21505]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:17:10 anton sshd[21505]: Failed password for invalid user support from 222.186.10.49 port 63528 ssh2\nSep 22 12:17:52 anton sshd[21519]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:17:54 anton sshd[21519]: Failed password for invalid user andrew from 222.186.10.49 port 5062 ssh2\nSep 22 12:18:31 anton sshd[21528]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:18:33 anton sshd[21528]: Failed password for invalid user office from 222.186.10.49 port 11124 ssh2\nSep 22 12:19:11 anton sshd[22290]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:19:12 anton sshd[22290]: Failed password for invalid user shop from 222.186.10.49 port 17178 ssh2\nSep 22 12:19:54 anton sshd[22312]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:19:56 anton sshd[22312]: Failed password for invalid user user from 222.186.10.49 port 23236 ssh2', 'ipjailmatches': 'Sep 22 12:02:14 anton sshd[18758]: Failed password for root from 222.186.10.49 port 59300 ssh2\nSep 22 12:02:54 anton sshd[18770]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:02:56 anton sshd[18770]: Failed password for invalid user gd from 222.186.10.49 port 65358 ssh2\nSep 22 12:03:34 anton sshd[18785]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:03:35 anton sshd[18785]: Failed password for invalid user ralf from 222.186.10.49 port 6908 ssh2\nSep 22 12:04:13 anton sshd[19604]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:04:15 anton sshd[19604]: Failed password for invalid user internet1 from 222.186.10.49 port 12962 ssh2\nSep 22 12:04:59 anton sshd[19628]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:05:02 anton sshd[19628]: Failed password for invalid user testftp from 222.186.10.49 port 19018 ssh2\nSep 22 12:05:37 anton sshd[19670]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:05:39 anton sshd[19670]: Failed password for invalid user fax from 222.186.10.49 port 25076 ssh2\nSep 22 12:06:14 anton sshd[19679]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:06:15 anton sshd[19679]: Failed password for invalid user test from 222.186.10.49 port 31134 ssh2\nSep 22 12:06:57 anton sshd[19691]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:06:59 anton sshd[19691]: Failed password for invalid user simedw from 222.186.10.49 port 37194 ssh2\nSep 22 12:07:37 anton sshd[19702]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:07:39 anton sshd[19702]: Failed password for invalid user linda from 222.186.10.49 port 43250 ssh2\nSep 22 12:08:18 anton sshd[19712]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:08:21 anton sshd[19712]: Failed password for invalid user samba from 222.186.10.49 port 49304 ssh2\nSep 22 12:09:00 anton sshd[19720]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:09:02 anton sshd[19720]: Failed password for invalid user heinrich from 222.186.10.49 port 55344 ssh2\nSep 22 12:09:39 anton sshd[20550]: Failed password for root from 222.186.10.49 port 61404 ssh2\nSep 22 12:10:21 anton sshd[20603]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:10:23 anton sshd[20603]: Failed password for invalid user arao from 222.186.10.49 port 2952 ssh2\nSep 22 12:10:59 anton sshd[20613]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:11:01 anton sshd[20613]: Failed password for invalid user upload from 222.186.10.49 port 9008 ssh2\nSep 22 12:11:40 anton sshd[20621]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:11:42 anton sshd[20621]: Failed password for invalid user master from 222.186.10.49 port 15066 ssh2\nSep 22 12:12:24 anton sshd[20631]: Failed password for irc from 222.186.10.49 port 21132 ssh2\nSep 22 12:13:06 anton sshd[20642]: Failed password for root from 222.186.10.49 port 27192 ssh2\nSep 22 12:13:45 anton sshd[20650]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:13:47 anton sshd[20650]: Failed password for invalid user amavis from 222.186.10.49 port 33250 ssh2\nSep 22 12:14:23 anton sshd[21417]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:14:25 anton sshd[21417]: Failed password for invalid user test from 222.186.10.49 port 39312 ssh2\nSep 22 12:15:05 anton sshd[21461]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:15:07 anton sshd[21461]: Failed password for invalid user fernandez from 222.186.10.49 port 45368 ssh2\nSep 22 12:15:47 anton sshd[21470]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:15:49 anton sshd[21470]: Failed password for invalid user wwwadmin from 222.186.10.49 port 51424 ssh2\nSep 22 12:16:27 anton sshd[21493]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:16:29 anton sshd[21493]: Failed password for invalid user abc from 222.186.10.49 port 57474 ssh2\nSep 22 12:17:08 anton sshd[21505]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:17:10 anton sshd[21505]: Failed password for invalid user support from 222.186.10.49 port 63528 ssh2\nSep 22 12:17:52 anton sshd[21519]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:17:54 anton sshd[21519]: Failed password for invalid user andrew from 222.186.10.49 port 5062 ssh2\nSep 22 12:18:31 anton sshd[21528]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:18:33 anton sshd[21528]: Failed password for invalid user office from 222.186.10.49 port 11124 ssh2\nSep 22 12:19:11 anton sshd[22290]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:19:12 anton sshd[22290]: Failed password for invalid user shop from 222.186.10.49 port 17178 ssh2\nSep 22 12:19:54 anton sshd[22312]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=222.186.10.49 \nSep 22 12:19:56 anton sshd[22312]: Failed password for invalid user user from 222.186.10.49 port 23236 ssh2', 'ipfailures': 393, 'ipjailfailures': 393})': Error unbanning 222.186.10.49
2020-09-22 13:15:04,921 fail2ban.utils [25636]: Level 39 7fc716142510 -- exec: ip route del unreachable 149.202.208.104
2020-09-22 13:15:04,922 fail2ban.utils [25636]: ERROR 7fc716142510 -- stderr: 'RTNETLINK answers: No such process'
2020-09-22 13:15:04,922 fail2ban.utils [25636]: ERROR 7fc716142510 -- returned 2
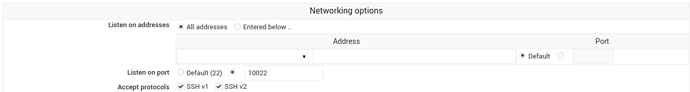
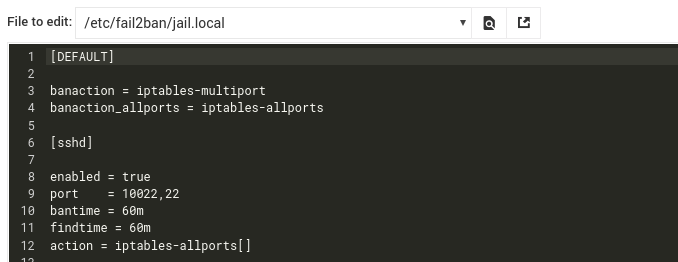
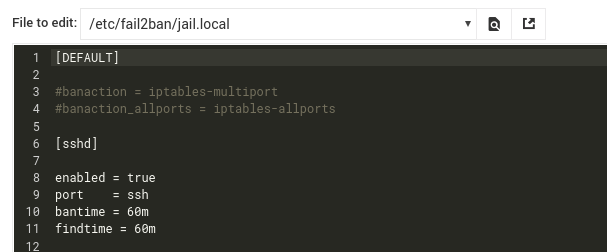
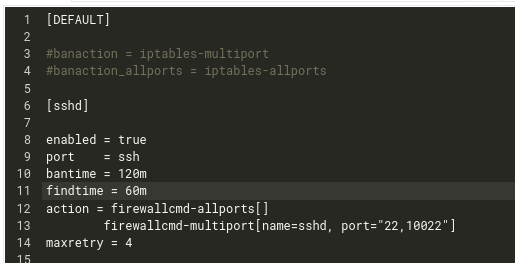
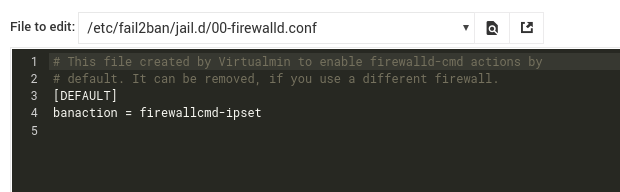
This is my current configuration:
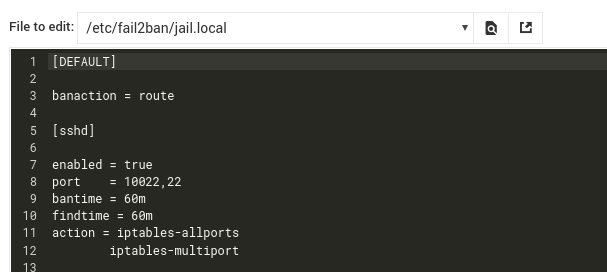
I have my sshd server running on port 10022.
what could be the problem? has anyone an idea of how to ban brute force attacks on ssh?