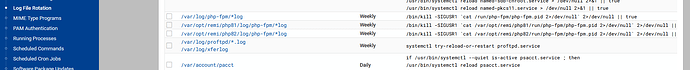
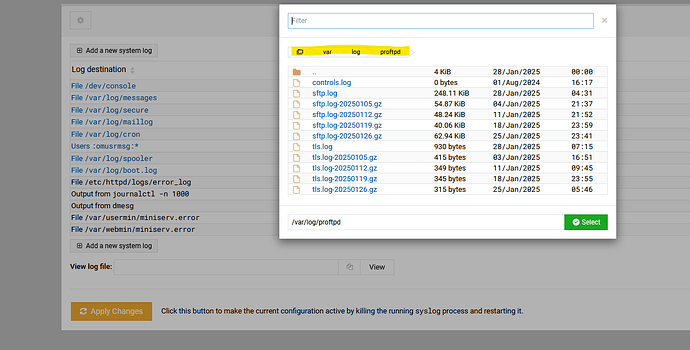
A little update: with ProFTP server OFF there is no sftp.log activity.
Right now ProFTP was running again, for 2 days apparently (creating 47Mb log data). I didn’t switch it ON. Do some updates may switch ProFTP ON?
Again I get 100+ entries of the same IP. A random sample (1 of 25000 from 3 days log data) from sftp.log:
2025-02-19 00:08:14,852 mod_sftp/1.1.1[1748855]: using '/etc/proftpd/ssh_host_ecdsa_key' as 256-bit ECDSA hostkey (256 bits)
2025-02-19 00:08:14,854 mod_sftp/1.1.1[1748855]: client (47.75.250.176:34940) connected to server (::ffff:130.255.77.161:2222) [session ID Z7Ug7oL/TaEvS/qwABqvd02K]
2025-02-19 00:08:14,855 mod_sftp/1.1.1[1748855]: sent server version 'SSH-2.0-mod_sftp'
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: received client version 'SSH-2.0-Go'
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: handling connection from SSH2 client 'Go'
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: + Session key exchange: curve25519-sha256@libssh.org
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: + Session host key algorithm: ecdsa-sha2-nistp256
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: + Session server hostkey: ecdsa-sha2-nistp256
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: + Session client-to-server encryption: aes128-ctr
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: + Session server-to-client encryption: aes128-ctr
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: + Session client-to-server MAC: hmac-sha2-256-etm@openssh.com
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: + Session server-to-client MAC: hmac-sha2-256-etm@openssh.com
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: + Session client-to-server compression: none
2025-02-19 00:08:15,893 mod_sftp/1.1.1[1748855]: + Session server-to-client compression: none
2025-02-19 00:08:18,772 mod_sftp/1.1.1[1748894]: using '/etc/proftpd/ssh_host_ecdsa_key' as 256-bit ECDSA hostkey (256 bits)
No cron entry…
crontab -l
sudo crontab -l
sudo ls /etc/cron.*
0,5,10,15,20,25,30,35,40,45,50,55 * * * * /etc/webmin/status/monitor.pl >/dev/null 2>&1
17 17 * * * /etc/webmin/virtualmin-awstats/awstats.pl d1.com
38 20 * * * /etc/webmin/virtualmin-awstats/awstats.pl d2.com
19 15 * * * /etc/webmin/virtualmin-awstats/awstats.pl d3.com
0,5,10,15,20,25,30,35,40,45,50,55 * * * * /etc/webmin/status/monitor.pl >/dev/null 2>&1
17 17 * * * /etc/webmin/virtualmin-awstats/awstats.pl d1.com
38 20 * * * /etc/webmin/virtualmin-awstats/awstats.pl d2.com
19 15 * * * /etc/webmin/virtualmin-awstats/awstats.pl d3.com
/etc/cron.d:
awstats certbot e2scrub_all ntpsec php
/etc/cron.daily:
apache2 apt-compat dpkg etckeeper fstrim logrotate man-db quota spamassassin
/etc/cron.hourly:
/etc/cron.monthly:
/etc/cron.weekly:
man-db
/etc/cron.yearly:
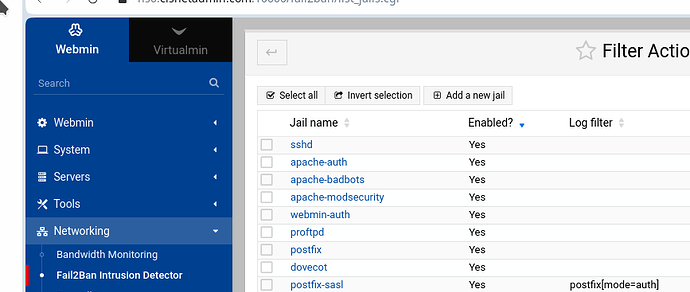
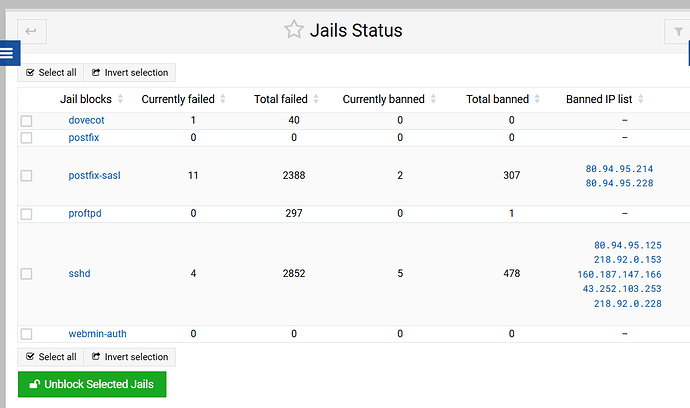
Can I add a daily cron to close proftp? And I still like to add some banning action to fail2ban.