Please turn off fail2ban. Its not needed with CSF.
Just going to jump in here.
I don’t use CSF, I use FirewallD, but I do use Fail2Ban and there are a couple of things I’ve noticed in this thread that may help.
The “already banned” message means your bans aren’t being enforced. Fail2ban is saying “hey, this IP did something wrong, but according to my database, it’s already banned.” The fact that the IP is being allowed to do something wrong when it’s already banned means the Firewall isn’t getting the instructions from Fail2Ban to block the IP address.
…Which brings me to the second point. If FirewallD is disabled, your ban action shouldn’t be firewallcmd-ipset, which, according to the logs you posted, it is. You probably need to change it to iptables-multiport or iptables-ipset in jail.local. This should tell Fail2ban to interact with your actual firewall.
Hope this helps.
Should I leave only CSF active??
That’s up to you, CSF uses Iptables and disables firewallD and fail2ban. DO NOT try to use them.
Just try it. There is a uninstall script if you not will to willing to go through the configuration.
Lets put it this way its not a newbies software.
The file has these entries. Can you tell me what to change?
[DEFAULT]
bantime = 1000m
findtime = 60s
destemail = admin@mail.info
sender = root
sendername = Fail2ban (Or whatever you want)
mta = sendmail
action = %(action_mw)s
[dovecot]
enabled = false
[postfix]
enabled = true
maxretry = 1
[postfix-sasl]
enabled = true
backend = systemd
journalmatch = _SYSTEMD_UNIT=postfix@-.service
maxretry = 3
[proftpd]
enabled = false
backend = auto
logpath = /var/log/proftpd/proftpd.log
maxretry = 2
[sshd]
enabled = true
maxretry = 3
[webmin-auth]
enabled = true
journalmatch = _SYSTEMD_UNIT=webmin.service
maxretry = 3
[other-allports-jail]
banaction = %(banaction_allports)s
[selinux-ssh]
enabled = true
maxretry = 3
[dropbear]
enabled = false
[apache-auth]
enabled = false
[apache-badbots]
enabled = false
[apache-noscript]
enabled = false
[apache-overflows]
enabled = false
[apache-nohome]
enabled = false
[apache-botsearch]
enabled = false
[apache-fakegooglebot]
enabled = false
[apache-modsecurity]
enabled = false
[apache-shellshock]
enabled = false
[openhab-auth]
enabled = false
[nginx-http-auth]
enabled = false
[nginx-limit-req]
enabled = false
[nginx-botsearch]
enabled = false
[php-url-fopen]
enabled = false
[suhosin]
enabled = false
[lighttpd-auth]
enabled = false
[roundcube-auth]
enabled = false
[openwebmail]
enabled = false
[horde]
enabled = false
[groupoffice]
enabled = false
[sogo-auth]
enabled = false
[tine20]
enabled = false
[drupal-auth]
enabled = false
[guacamole]
enabled = false
[monit]
enabled = false
[froxlor-auth]
enabled = false
[squid]
enabled = false
[3proxy]
enabled = false
[pure-ftpd]
enabled = false
[gssftpd]
enabled = false
[wuftpd]
enabled = false
[vsftpd]
enabled = false
[assp]
enabled = false
[courier-smtp]
enabled = false
[postfix-rbl]
enabled = true
maxretry = 3
[sendmail-auth]
enabled = false
[sendmail-reject]
enabled = false
[qmail-rbl]
enabled = false
maxretry = 3
[sieve]
enabled = false
[solid-pop3d]
enabled = false
[exim]
enabled = false
[exim-spam]
enabled = false
[kerio]
enabled = false
[courier-auth]
enabled = false
[perdition]
enabled = false
[squirrelmail]
enabled = false
[cyrus-imap]
enabled = false
[uwimap-auth]
enabled = false
[named-refused]
enabled = false
[nsd]
enabled = false
[asterisk]
enabled = false
[freeswitch]
enabled = false
[znc-adminlog]
enabled = false
[mysqld-auth]
enabled = false
[mongodb-auth]
enabled = false
[recidive]
enabled = false
[pam-generic]
enabled = false
[xinetd-fail]
enabled = false
[stunnel]
enabled = false
[ejabberd-auth]
enabled = false
[counter-strike]
enabled = false
[softethervpn]
enabled = false
[gitlab]
enabled = false
[grafana]
enabled = false
[bitwarden]
enabled = false
[centreon]
enabled = false
[nagios]
enabled = false
[oracleims]
enabled = false
[directadmin]
enabled = true
maxretry = 3
[portsentry]
enabled = false
[pass2allow-ftp]
enabled = false
action = %(action_)s[actionstart_on_demand=false, returntype=%(returntype)s, actionrepair_on_unban=true, blocktype=%(blocktype)s]
maxretry = 3
[murmur]
enabled = false
[screensharingd]
enabled = false
[haproxy-http-auth]
enabled = false
[slapd]
enabled = false
[domino-smtp]
enabled = false
[phpmyadmin-syslog]
enabled = false
[zoneminder]
enabled = false
[traefik-auth]
enabled = false
[scanlogd]
enabled = false
maxretry = 3
firewallD is disabled, I’m not trying to have both csf and firewallD. I want to know, can’t I have csf and fail2ban to in the vps?
Should I turn on firewallD with file2ban and remove csf?
You have gone away from the stock virtualmin install by installing csf, the default setup works out of the box so by installing csf you were, perhaps, trying to fix something that isn’t broken. As firewalld/fail2ban do the same job as csf the choice is yours either disable both fail2ban and firewalld and use csf or disable csf and use firewalld/fail2ban the choice is yours you can not use both
NO you can’t. Why the obsession with fail2ban.
CSF will do the bans for you using iptables.
If you want to use fail2ban the uninstall CSF.
ON firewallD off CSF and I see good results??
I have a jail time of 3 minutes, so is it working properly now?
2024-05-23 16:06:03,114 fail2ban.actions [698]: NOTICE [postfix-sasl] Ban 194.169.175.17
2024-05-23 16:06:02,516 fail2ban.filter [698]: INFO [postfix-sasl] Found 194.169.175.17 - 2024-05-23 16:06:02
2024-05-23 16:05:59,087 fail2ban.actions [698]: NOTICE [postfix-sasl] Unban 194.169.175.10
2024-05-23 16:05:59,073 fail2ban.actions [698]: NOTICE [postfix-sasl] Unban 194.169.175.20
2024-05-23 16:05:54,975 fail2ban.actions [698]: NOTICE [postfix-sasl] Ban 194.169.175.10
2024-05-23 16:05:54,361 fail2ban.actions [698]: NOTICE [postfix-sasl] Ban 194.169.175.20
2024-05-23 16:05:54,266 fail2ban.filter [698]: INFO [postfix-sasl] Found 194.169.175.10 - 2024-05-23 16:05:54
2024-05-23 16:05:54,013 fail2ban.filter [698]: INFO [postfix-sasl] Found 194.169.175.20 - 2024-05-23 16:05:53
Fail2Ban is essentially LFD (Login Failure Daemon) in CSF. It does exactly what Fail2Ban does. There is no need to have Fail2Ban if you are using CSF, period!
As an expert in virtualmin, which one do you recommend I leave for better security? I see a lot of attacks on my vps postfix_sals
ON firewallD off CSF and I see good results??
I have a jail time of 3 minutes, so is it working properly now?
Hmm, I can’t see how that possible.
What do you see here. (bans are done with LDF)
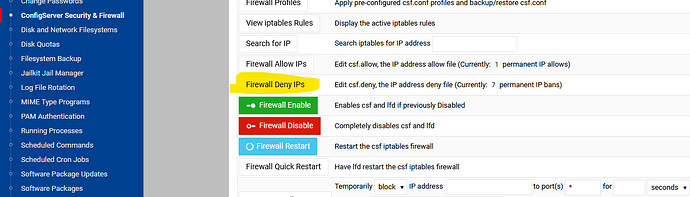
Click into it
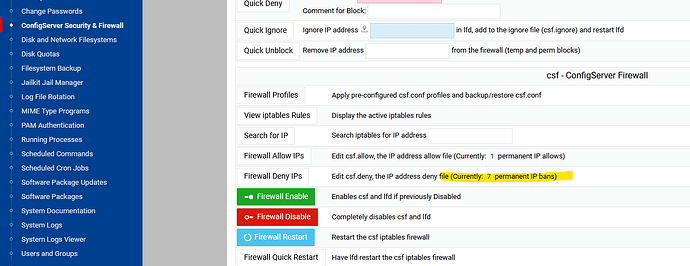
Edit csf.deny, the IP address deny file (Currently: 2 permanent IP bans)
What file is the second image you have uploaded?
Hmm, I can’t see how that possible.
What do you see here. (bans are done with LDF)
I am guessing the op disabled csf and enabled firewalld and fail2ban to get that result
Reboot for Fail2ban error…
What should I do about the time error?
2024-05-23 18:01:40,500 fail2ban.filter [695]: WARNING [postfix-sasl] Please check jail has possibly a timezone issue. Line with odd timestamp: (‘’, ‘2024-05-23T17:59:09.895096’, ‘myhostname postfix/anvil[3225]: statistics: max connection rate 1/60s for (smtp:194.169.175.20) at May 23 17:52:33’)
2024-05-23 18:01:40,500 fail2ban.filter [695]: WARNING [postfix-sasl] Simulate NOW in operation since found time has too large deviation 1716476349.895096 ~ 1716476500.500114 +/- 60
2024-05-23 18:01:40,483 fail2ban.filter [695]: WARNING [selinux-ssh] Please check jail has possibly a timezone issue. Line with odd timestamp: (‘’, ‘2024-05-23T18:00:02.564053’, ‘cp.vps-server.info CRON[9252]: pam_unix(cron:session): session closed for user root’)
2024-05-23 18:01:40,483 fail2ban.filter [695]: WARNING [selinux-ssh] Simulate NOW in operation since found time has too large deviation 1716476402.564053 ~ 1716476500.483581 +/- 60
The message is invalid, I restarted the server a second time and it’s ok.
As an expert in virtualmin, which one do you recommend I leave for better security? I see a lot of attacks on my vps postfix_sals
Virtualmin isn’t involved, but either option works. LFD in CSF is a more powerful and configurable tool than Fail2Ban. However, both ultimately serve the same purpose—significantly reducing the chances of successful brute force attacks.
Postfix and other services will always be “under attack” by bot-nets. This is normal for any server facing the internet.
The only thing you should really worry about is making sure every user on your server has a super strong password for each service they use.
I am the only vps user. Hey, tell me to put a very difficult code in the services for security…
I tried an ssh attack from my pc with a wrong password. He bans me but lets me do another attack. Why are you doing this, is this some kind of setup? (85.73.**** myip.
2024-05-23 18:25:26,384 fail2ban.actions [703]: WARNING [sshd] 85.73. already banned
2024-05-23 18:25:26,384 fail2ban.actions [703]: WARNING [sshd] 85.73. already banned
2024-05-23 18:25:26,310 fail2ban.filter [703]: INFO [sshd] Found 85.73. - 2024-05-23 18:25:26
2024-05-23 18:25:26,310 fail2ban.filter [703]: INFO [sshd] Found 85.73. - 2024-05-23 18:25:25
2024-05-23 18:25:23,178 fail2ban.actions [703]: WARNING [sshd] 85.73. already banned
2024-05-23 18:25:22,846 fail2ban.filter [703]: INFO [sshd] Found 85.73.**** - 2024-05-23 18:25:22
2024-05-23 18:25:18,571 fail2ban.actions [703]: WARNING [sshd] 85.73. already banned
2024-05-23 18:25:18,347 fail2ban.filter [703]: INFO [sshd] Found 85.73. - 2024-05-23 18:25:17
2024-05-23 18:25:14,565 fail2ban.actions [703]: WARNING [sshd] 85.73. already banned
2024-05-23 18:25:14,551 fail2ban.filter [703]: INFO [sshd] Found 85.73. - 2024-05-23 18:25:14