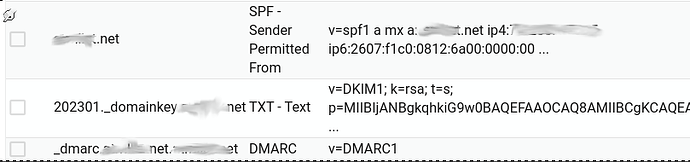
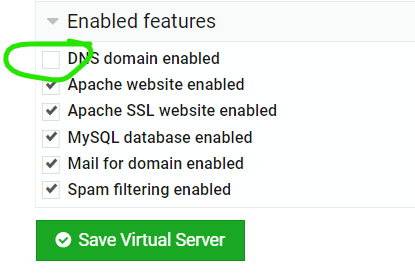
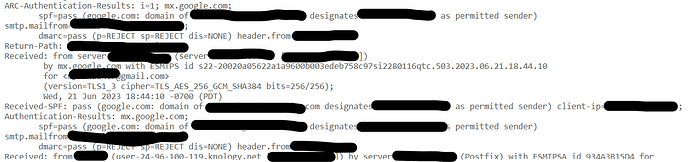
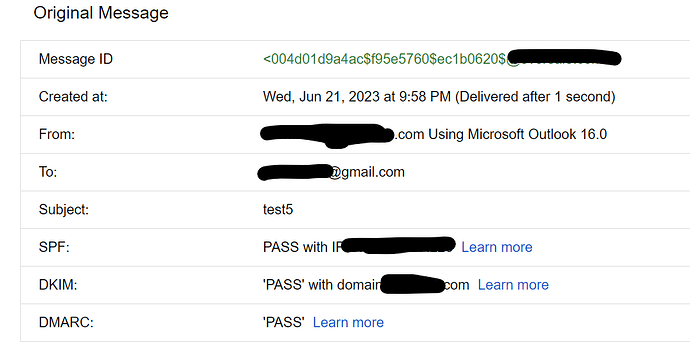
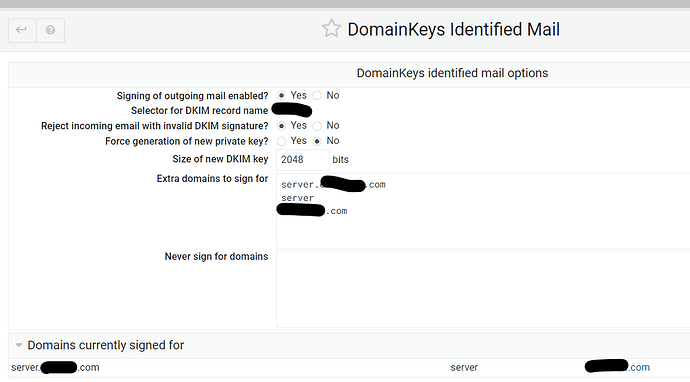
ok, so outgoing email is now signed.
but incoming, still got a persistent spammer, ugh
see below (sorry for the long post)
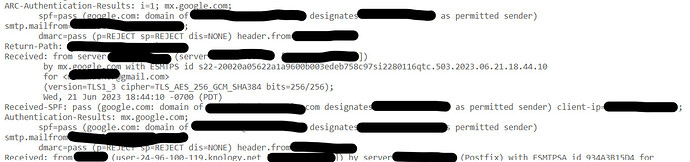
see DKIM_INVALID, dkim=fail. so why did Virtualmin allow this to pass ?
Return-Path: <>
X-Spam-Checker-Version: SpamAssassin 3.4.2 (2018-09-13) on server.domain.com
X-Spam-Level: ****
X-Spam-Status: No, score=4.0 required=5.0 tests=BAD_ENC_HEADER,BAYES_00,
DKIM_INVALID,DKIM_SIGNED,HTML_FONT_SIZE_HUGE,HTML_IMAGE_ONLY_32,
HTML_MESSAGE,MIME_HTML_ONLY,RCVD_IN_BL_SPAMCOP_NET,RCVD_IN_MSPIKE_BL,
RCVD_IN_MSPIKE_L3,RCVD_IN_SBL,RCVD_IN_SBL_CSS,RDNS_NONE,SPF_HELO_NONE,
T_SCC_BODY_TEXT_LINE,URIBL_BLOCKED autolearn=no autolearn_force=no
version=3.4.2
X-Original-To: info@domain.com
Delivered-To: name-domain.com@localhost.localdomain
Received: by server.domain.com (Postfix)
id 4C509B1606; Thu, 22 Jun 2023 13:10:31 +0000 (UTC)
Delivered-To: info-domain.com@localhost.localdomain
Received: from o1.ptr6955.ncare.nl (unknown [103.186.116.160])
by server.domain.com (Postfix) with ESMTP id 075F2B15D4
for info@domain.com; Thu, 22 Jun 2023 13:10:31 +0000 (UTC)
Authentication-Results: server.domain.com;
dkim=fail reason=“signature verification failed” (1024-bit key; unprotected) header.d=news.foodnetwork.com header.i=@news.foodnetwork.com header.b=“hNB+JCsJ”;
dkim-atps=neutral
Received: from AS4P250MB0416.EURP250.PROD.OUTLOOK.COM (2603:10a6:20b:4c3::20)
by DB9P250MB0451.EURP250.PROD.OUTLOOK.COM with HTTPS; Tue, 20 Jun 2023
19:48:22 +0000
Received: from MW4PR03CA0011.namprd03.prod.outlook.com (2603:10b6:303:8f::16)
by AS4P250MB0416.EURP250.PROD.OUTLOOK.COM (2603:10a6:20b:4c3::20) with
Microsoft SMTP Server (version=TLS1_2,
cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.6477.42; Tue, 20 Jun
2023 19:48:19 +0000
Received: from MW2NAM10FT104.eop-nam10.prod.protection.outlook.com
(2603:10b6:303:8f:cafe::85) by MW4PR03CA0011.outlook.office365.com
(2603:10b6:303:8f::16) with Microsoft SMTP Server (version=TLS1_2,
cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.6500.37 via Frontend
Transport; Tue, 20 Jun 2023 19:48:19 +0000
Authentication-Results: spf=pass (sender IP is 137.22.224.206)
smtp.mailfrom=news.foodnetwork.com; dkim=pass (signature was verified)
header.d=news.foodnetwork.com;dmarc=pass action=none
header.from=news.foodnetwork.com;compauth=pass reason=100
Received-SPF: Pass (protection.outlook.com: domain of news.foodnetwork.com
designates 137.22.224.206 as permitted sender)
receiver=protection.outlook.com; client-ip=137.22.224.206;
helo=137.22.224.206.jfk.braze.com; pr=C
Received: from 137.22.224.206.jfk.braze.com (137.22.224.206) by
MW2NAM10FT104.mail.protection.outlook.com (10.13.155.208) with Microsoft SMTP
Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id
15.20.6521.23 via Frontend Transport; Tue, 20 Jun 2023 19:48:19 +0000
X-IncomingTopHeaderMarker:
OriginalChecksum:7497CA1351BF1AE90AD024580DF24266AE9476857639FD43F5D7278D8E2D8307;UpperCasedChecksum:5A0DBBE578547D960C0DEDB16AEBF189F0E37A2BE9BE347D2AE1BC6C8200A726;SizeAsReceived:1100;Count:10
X-MSFBL: tkJ03dJvirEGSg6lqoYLzQcXIvikVF03yLgDB9bMqoE=|eyJyIjoiam5hbm1hcmF
3YUBob3RtYWlsLmNvbSIsImN1c3RvbWVyX2lkIjoiMjY2NjkzIiwibWVzc2FnZV9
pZCI6IjY0OTE3ZjAyOTI2NGY5ZjY4YjUwIiwic3ViYWNjb3VudF9pZCI6Ijc5MyI
sInRlbmFudF9pZCI6InNwYyJ9
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=news.foodnetwork.com; s=scph0223; t=1687290495;
i=@news.foodnetwork.com;
bh=V/HbgTmtsoTCJpCP3zvdxiDXpjdslAdzSpPPFyW05+4=;
h=To:Message-ID:Date:Content-Type:Subject:From:From:To:Cc:Subject;
b=hNB+JCsJtnKsjDE0quCKJ6MolwJ7TIcjcBO6u38dwEfqfprNPRvAUhHLylQCh0HGy
eULufuAMC7OTH/mQQVOgoIinG+zSU8rmT6a64pdFt9Om8W9ZFexI7BN2GMcZLFbxxJ
K3ywnqCjxyUtv5AcXHDlRapElTspeg8kSS+evjII=
To: info info@domain.com
Message-ID: B8.05.47712.khEKK18M@jl.mta1vrest.cc.prd.sparkpost
Date: Thu, 22 Jun 2023 15:10:24 +0200
Content-Type: text/html;
Subject: =?UTF-8?Q?Congrats! You’ve Been Selected For $100 CVS Reward?=
From: “=?UTF-8?Q?CVS Shipment?=” info@domain.com
X-IncomingHeaderCount: 10
X-MS-Exchange-Organization-ExpirationStartTime: 20 Jun 2023 19:48:19.2523
(UTC)
X-MS-Exchange-Organization-ExpirationStartTimeReason: OriginalSubmit
X-MS-Exchange-Organization-ExpirationInterval: 1:00:00:00.0000000
X-MS-Exchange-Organization-ExpirationIntervalReason: OriginalSubmit
X-MS-Exchange-Organization-Network-Message-Id:
ac0455e7-aecb-49ac-0382-08db71c74c1e
X-EOPAttributedMessage: 0
X-EOPTenantAttributedMessage: 84df9e7f-e9f6-40af-b435-aaaaaaaaaaaa:0
X-MS-Exchange-Organization-MessageDirectionality: Incoming
X-MS-PublicTrafficType: Email
X-MS-TrafficTypeDiagnostic:
MW2NAM10FT104:EE_|AS4P250MB0416:EE_|DB9P250MB0451:EE_
X-MS-Exchange-Organization-AuthSource:
MW2NAM10FT104.eop-nam10.prod.protection.outlook.com
X-MS-Exchange-Organization-AuthAs: Anonymous
X-MS-UserLastLogonTime: 6/20/2023 5:38:23 PM
X-MS-Office365-Filtering-Correlation-Id: ac0455e7-aecb-49ac-0382-08db71c74c1e
X-MS-Exchange-EOPDirect: true
X-Sender-IP: 137.22.224.206
X-SID-PRA: info@domain.com
X-SID-Result: PASS
X-MS-Exchange-Organization-PCL: 2
X-MS-Exchange-Organization-SCL: 1
X-Microsoft-Antispam: BCL:0;
X-MS-Exchange-CrossTenant-OriginalArrivalTime: 20 Jun 2023 19:48:19.1585
(UTC)
X-MS-Exchange-CrossTenant-Network-Message-Id: ac0455e7-aecb-49ac-0382-08db71c74c1e
X-MS-Exchange-CrossTenant-Id: 84df9e7f-e9f6-40af-b435-aaaaaaaaaaaa
X-MS-Exchange-CrossTenant-AuthSource:
MW2NAM10FT104.eop-nam10.prod.protection.outlook.com
X-MS-Exchange-CrossTenant-AuthAs: Anonymous
X-MS-Exchange-CrossTenant-FromEntityHeader: Internet
X-MS-Exchange-CrossTenant-RMS-PersistedConsumerOrg:
00000000-0000-0000-0000-000000000000
X-MS-Exchange-Transport-CrossTenantHeadersStamped: AS4P250MB0416
X-MS-Exchange-Transport-EndToEndLatency: 00:00:03.6097526
X-MS-Exchange-Processed-By-BccFoldering: 15.20.6477.035
X-Microsoft-Antispam-Mailbox-Delivery:
….
X-Message-Info:
….
X-Message-Delivery: Vj0xLjE7dXM9MDtsPTA7YT0xO0Q9MTtHRD0xO1NDTD0z
X-Microsoft-Antispam-Message-Info:
….
MIME-Version: 1.0