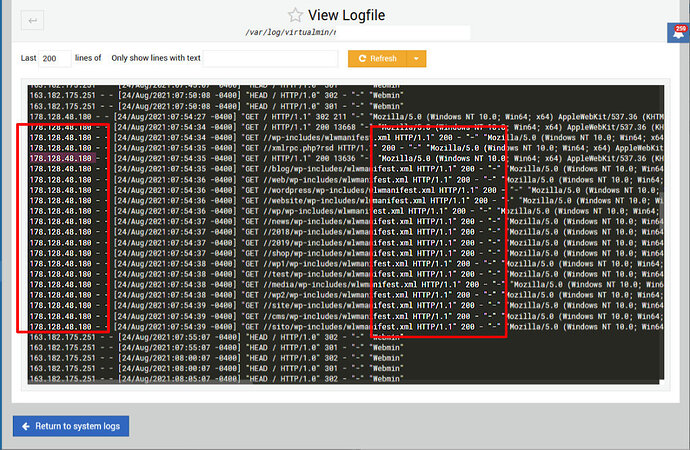
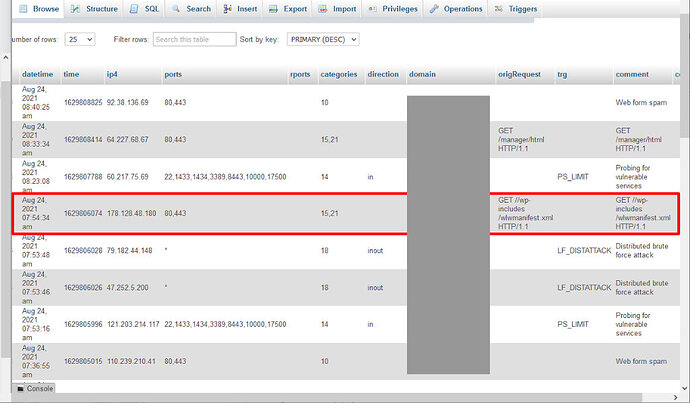
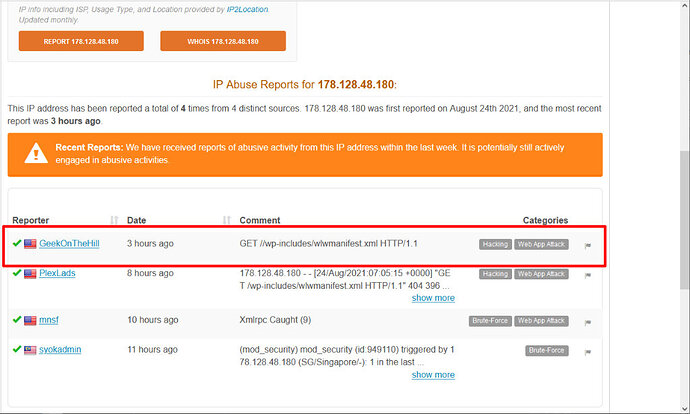
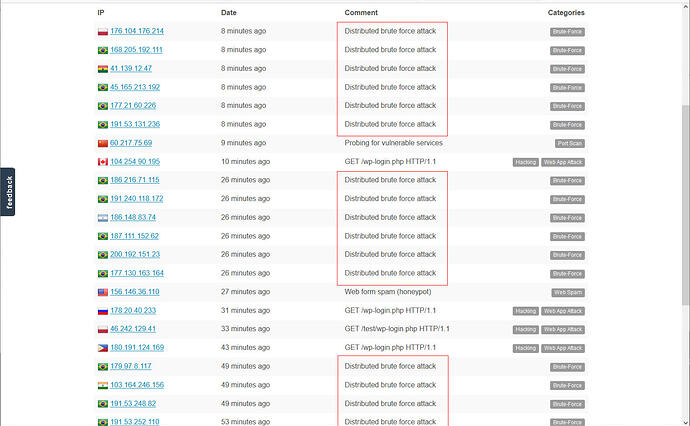
I update this from time to time based on current attack trends. It’s a list of .htaccess entries to redirect miscreants looking for vulnerable pages on CMS platforms to a trap page that blocks and reports them.
Obviously don’t use any pages or directories that actually exist on the site. This is really only useful on hand-coded sites that bots attack assuming they’re running on a CMS.
RewriteEngine On
RewriteCond %{REQUEST_URI} /admin.php [NC,OR]
RewriteCond %{REQUEST_URI} /install.php [NC,OR]
RewriteCond %{REQUEST_URI} /lequ.php [NC,OR]
RewriteCond %{REQUEST_URI} /login.php [NC,OR]
RewriteCond %{REQUEST_URI} /setup.php [NC,OR]
RewriteCond %{REQUEST_URI} /shell.php [NC,OR]
RewriteCond %{REQUEST_URI} /user.php [NC,OR]
RewriteCond %{REQUEST_URI} /webconfig.txt.php [NC,OR]
RewriteCond %{REQUEST_URI} /wp-config.php [NC,OR]
RewriteCond %{REQUEST_URI} /wp-contacts.php [NC,OR]
RewriteCond %{REQUEST_URI} /wp-login.php [NC,OR]
RewriteCond %{REQUEST_URI} /xmlrpc [NC,OR]
RewriteCond %{REQUEST_URI} /xmlrpc.php [NC,OR]
RewriteCond %{REQUEST_URI} ^/2020/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/2019/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/admin/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/administrator/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/config/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/blog/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/cms/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/data/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/demo/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/fckeditor/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/.git/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/inc/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/install/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/magento/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/manager/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/news/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/plus/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/setup/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/shop/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/site/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/staging/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/templates/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/test/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/web/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/website/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/wordpress/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/wp/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/wp1/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/wp2/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/wp-admin/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/wp-contacts/(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^/wp-includes/(.*)$ [NC]
RewriteRule .* https://example.com/trap-page.php?req=%{THE_REQUEST} [L]
Many (but not all) of the entries on my blocklists and my AbuseIPDB page are generated this way. The trap page enters them into the database from whence the blocklists are created, as well as reports them to AbuseIPDB.
Richard