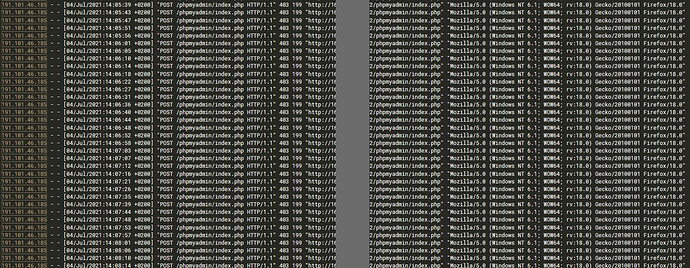
is this what i am thinking it is? started around 10 hours ago…
What does Fail2Ban show? It is your brute force attack protector.
fail2ban is probably not monitoring the Apache logs (it does not by default in a Virtualmin install for a variety of reasons). It does appear to be a brute force attempt to login to phpmyadmin, assuming that’s not an IP you recognize.
If you’re worried about it and want to do something, you have a few options.
You could setup fail2ban to monitor that log, if you wanted active blocking. If it’s just one IP, you could just block that one IP manually. I would hope phpmyadmin would also have brute force protections built in (I don’t know, I don’t use it, I use the Webmin database modules).
And, if you always know what IP(s) you will be logging into phpmyadmin with, you could block all but that IP.
Then again, I just noticed those are 403 errors, which probably means phpmyadmin isn’t even there, I guess? (Or does it switch to 403 on failed auth, maybe meaning its own protections have kicked in? Again, I have literally no idea what phpmyadmin does.)
Yeah, i blocked that IP with htaccess.
I decided to modified phpmyadmin index page. I can revert these changes when i need to access.
P.S. I was digging through access log and i saw many brute-force attempts from different IPs. I reported them all.
I totally agree with Joe. Make sure that Fail2Ban is monitoring what you need it to, so that brute force attacks are stopped dead in their tracks.
That typically falls on deaf ears because IP’s are used over and over by different entities and brute force attackers swop out IP’s with each attempt.
It’s why I run Cloudflare. It stops most all of that automatically. I have better things to do than spend hours on end playing whack-a-mole with attackers.
I strongly suggest that you stay away from Cloudflare. It makes it impossible to visit a site from another country. It is a royal PITA and I would not wish it on my worse enemy. The same for Jetpack, which Virtualmin has fallen prey to. It is all very sad.
There is no substitute for doing things properly as a good sysadmin, and not relying upon draconian measures by outside “services” which are not a service to any but the lazy.
That only happens if you set it to block that country. I and millions of others have used it for years and I’ve never seen or heard of anybody having that problem that didn’t intentionally set it up that way.
@KitchM well I wrote some regex for f2b which prevents brute force for Apache and PMA (phpmyadmin) and have them implement on my own server and 100s others however it’s private work even it’s open source under GPL license… I found out many would like to resel my solution which they did but removed me from licence so I offer this as private hire solution licenced to my mane. in end of the day it’s easy you can do it too, you just need to understand f2b. happy days all.
or just open support ticket with virtualmin folks, I’m sure they cover you at 100%
he is one of those I need for free…I would classify this as a spam if it’s up to me. best way is to not fight it refers to official channels and give it out to virtualmin folks 
This topic was automatically closed 60 days after the last reply. New replies are no longer allowed.