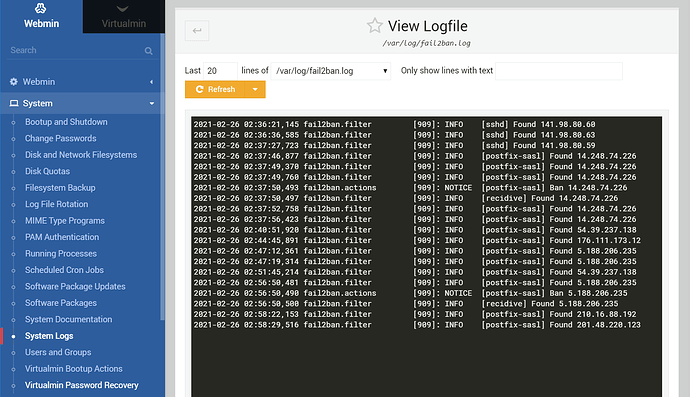
Hello,
I checked my /var/log/maillog
There are some ips that are trying to a do a SASL LOGIN authentication all the time.
I think it is called brute force attack.
Feb 18 17:29:10 hostname postfix/smtpd[12470]: connect from unknown[212.70.149.54]
Feb 18 17:29:20 hostname postfix/smtpd[12470]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:29:21 hostname postfix/smtpd[12470]: disconnect from unknown[212.70.149.54]
Feb 18 17:29:34 hostname postfix/smtpd[18245]: connect from unknown[212.70.149.54]
Feb 18 17:29:44 hostname postfix/smtpd[18245]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:29:45 hostname postfix/smtpd[18245]: disconnect from unknown[212.70.149.54]
Feb 18 17:29:58 hostname postfix/smtpd[12470]: connect from unknown[212.70.149.54]
Feb 18 17:30:08 hostname postfix/smtpd[12470]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:30:09 hostname postfix/smtpd[12470]: disconnect from unknown[212.70.149.54]
Feb 18 17:30:22 hostname postfix/smtpd[18245]: connect from unknown[212.70.149.54]
Feb 18 17:30:23 hostname postfix/smtpd[22879]: warning: hostname net6-ip210.linkbg.com does not resolve to address 87.246.7.210: Name or service not known
Feb 18 17:30:23 hostname postfix/smtpd[22879]: connect from unknown[87.246.7.210]
Feb 18 17:30:31 hostname postfix/smtpd[18245]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:30:33 hostname postfix/smtpd[18245]: disconnect from unknown[212.70.149.54]
Feb 18 17:30:45 hostname postfix/smtpd[12470]: connect from unknown[212.70.149.54]
Feb 18 17:30:49 hostname postfix/smtpd[22879]: lost connection after AUTH from unknown[87.246.7.210]
Feb 18 17:30:49 hostname postfix/smtpd[22879]: disconnect from unknown[87.246.7.210]
Feb 18 17:30:55 hostname postfix/smtpd[12470]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:30:56 hostname postfix/smtpd[12470]: disconnect from unknown[212.70.149.54]
Feb 18 17:31:09 hostname postfix/smtpd[18245]: connect from unknown[212.70.149.54]
Feb 18 17:31:18 hostname postfix/smtpd[18245]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:31:18 hostname postfix/smtpd[18245]: disconnect from unknown[212.70.149.54]
Feb 18 17:31:33 hostname postfix/smtpd[12470]: connect from unknown[212.70.149.54]
Feb 18 17:31:42 hostname postfix/smtpd[12470]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:31:44 hostname postfix/smtpd[12470]: disconnect from unknown[212.70.149.54]
Feb 18 17:31:57 hostname postfix/smtpd[18245]: connect from unknown[212.70.149.54]
Feb 18 17:32:07 hostname postfix/smtpd[18245]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:32:07 hostname postfix/smtpd[18245]: disconnect from unknown[212.70.149.54]
Feb 18 17:32:20 hostname postfix/smtpd[12470]: connect from unknown[212.70.149.54]
Feb 18 17:32:30 hostname postfix/smtpd[12470]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:32:31 hostname postfix/smtpd[12470]: disconnect from unknown[212.70.149.54]
Feb 18 17:32:43 hostname postfix/smtpd[25098]: warning: hostname net6-ip210.linkbg.com does not resolve to address 87.246.7.210: Name or service not known
Feb 18 17:32:43 hostname postfix/smtpd[25098]: connect from unknown[87.246.7.210]
Feb 18 17:32:44 hostname postfix/smtpd[18245]: connect from unknown[212.70.149.54]
Feb 18 17:32:54 hostname postfix/smtpd[18245]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:32:55 hostname postfix/smtpd[18245]: disconnect from unknown[212.70.149.54]
Feb 18 17:33:08 hostname postfix/smtpd[12470]: connect from unknown[212.70.149.54]
Feb 18 17:33:18 hostname postfix/smtpd[12470]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:33:19 hostname postfix/smtpd[12470]: disconnect from unknown[212.70.149.54]
Feb 18 17:33:23 hostname postfix/smtpd[25098]: warning: unknown[87.246.7.210]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:33:28 hostname postfix/smtpd[25098]: lost connection after AUTH from unknown[87.246.7.210]
Feb 18 17:33:28 hostname postfix/smtpd[25098]: disconnect from unknown[87.246.7.210]
Feb 18 17:33:32 hostname postfix/smtpd[18245]: connect from unknown[212.70.149.54]
Feb 18 17:33:41 hostname postfix/smtpd[18245]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:33:42 hostname postfix/smtpd[18245]: disconnect from unknown[212.70.149.54]
Feb 18 17:33:55 hostname postfix/smtpd[12470]: connect from unknown[212.70.149.54]
Feb 18 17:34:05 hostname postfix/smtpd[12470]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:34:06 hostname postfix/smtpd[12470]: disconnect from unknown[212.70.149.54]
Feb 18 17:34:19 hostname postfix/smtpd[18245]: connect from unknown[212.70.149.54]
Feb 18 17:34:29 hostname postfix/smtpd[18245]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:34:30 hostname postfix/smtpd[18245]: disconnect from unknown[212.70.149.54]
Feb 18 17:34:43 hostname postfix/smtpd[12470]: connect from unknown[212.70.149.54]
Feb 18 17:34:53 hostname postfix/smtpd[12470]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:34:54 hostname postfix/smtpd[12470]: disconnect from unknown[212.70.149.54]
Feb 18 17:35:03 hostname postfix/smtpd[25098]: warning: hostname net6-ip210.linkbg.com does not resolve to address 87.246.7.210: Name or service not known
Feb 18 17:35:03 hostname postfix/smtpd[25098]: connect from unknown[87.246.7.210]
Feb 18 17:35:07 hostname postfix/smtpd[18245]: connect from unknown[212.70.149.54]
Feb 18 17:35:17 hostname postfix/smtpd[18245]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:35:17 hostname postfix/smtpd[18245]: disconnect from unknown[212.70.149.54]
Feb 18 17:35:30 hostname postfix/smtpd[12470]: connect from unknown[212.70.149.54]
Feb 18 17:35:40 hostname postfix/smtpd[12470]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:35:41 hostname postfix/smtpd[12470]: disconnect from unknown[212.70.149.54]
Feb 18 17:35:43 hostname postfix/smtpd[25098]: warning: unknown[87.246.7.210]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:35:48 hostname postfix/smtpd[25098]: lost connection after AUTH from unknown[87.246.7.210]
Feb 18 17:35:48 hostname postfix/smtpd[25098]: disconnect from unknown[87.246.7.210]
Feb 18 17:35:54 hostname postfix/smtpd[18245]: connect from unknown[212.70.149.54]
Feb 18 17:36:04 hostname postfix/smtpd[18245]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:36:05 hostname postfix/smtpd[18245]: disconnect from unknown[212.70.149.54]
Feb 18 17:36:18 hostname postfix/smtpd[12470]: connect from unknown[212.70.149.54]
Feb 18 17:36:27 hostname postfix/smtpd[12470]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:36:29 hostname postfix/smtpd[12470]: disconnect from unknown[212.70.149.54]
Feb 18 17:36:42 hostname postfix/smtpd[18245]: connect from unknown[212.70.149.54]
Feb 18 17:36:51 hostname postfix/smtpd[18245]: warning: unknown[212.70.149.54]: SASL LOGIN authentication failed: authentication failure
Feb 18 17:36:52 hostname postfix/smtpd[18245]: disconnect from unknown[212.70.149.54]
How can avoid this login attempts?
Thank you.
Regards.
Operating system: CentOS
OS version: CentOS7-2009