Hi, I’m sorry for the inconvenience with this post but, I just received this email from your server https://dehoust-co.de/ wtf ?? What is happening, why is this email coming from this source? If anyone can help Thank you in advance.
Means little as forgeries have been common for many years, you need to check the headers to see what is really going on.
That’s not our server. What makes you think it’s ours?
Breathe in, breathe out…
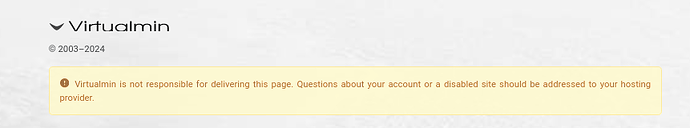
Most probably because the website sports a Virtualmin placeholder page.
I mean, yeah, but:
We make software (free software, at that, we don’t even know who hosts the vast majority of sites using Virtualmin), we’re not a hosting provider.
How should we make that more clear on the default pages?
Big, bold red letters. ![]()
I do understand the necessity spreading the word about your amazing product but you should consider a neutral placeholder instead. Especially regarding the growing amount of cyber threats. It never was easier to spin up a fake website. And we all know that people hardly read to the end and/or make the effort to understand and do some research before reaching out to the wrong endpoint.
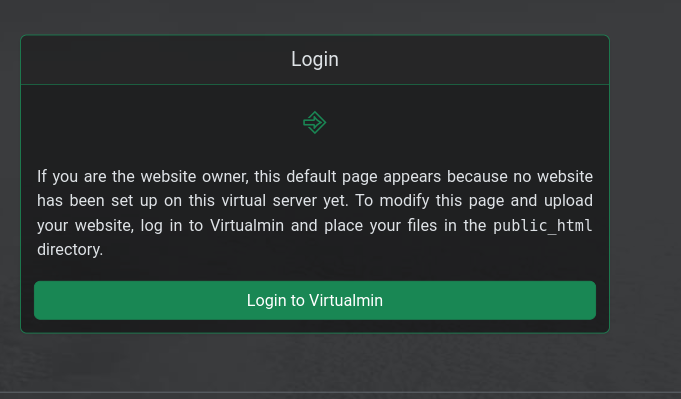
I thought this covers it … it indicates the person(s) who own the domain should add a website
It takes one to know one. That never works and only leads to disappointment. ![]()
I don’t understand most likely lost in translation
Hi there,
This means spam as there are no real FULL names
Don’t judge others by your own standards. Because you do, doesn’t necessarily mean others do the same. Hence, to avoid disappointment, make it crystal-clear and foolproof by either slapping an H1 DIV on the placeholder page or make it neutral with no referrals to Virtualmin at all.