**Operating system: Debian *
OS version: 10 - Virtualmin 6.1.5
Well i am trying to setup Fail2ban… better…
but always some IP pass the smtpd wihout banned (and keep trying)…
Mar 18 08:16:22 m***** postfix/smtpd[29171]: warning: unknown[87.246.7.226]: SASL LOGIN authentication failed: authentication failure
My postfix.conf is:
Fail2Ban filter for selected Postfix SMTP rejections
[INCLUDES]
Read common prefixes. If any customizations available – read them from
common.local
before = common.conf
[Definition]
_daemon = postfix(-\w+)?/\w+(?:/smtp[ds])?
_port = (?::\d+)?prefregex = ^%(__prefix_line)s<mdpr-> .+$
mdpr-normal = (?:NOQUEUE: reject:|improper command pipelining after \S+)
mdre-normal=^RCPT from [[1][]%(_port)s: 55[04] 5.7.1\s
^RCPT from [[2][]%(_port)s: 45[04] 4.7.1 (?:Service unavailable\b|Client host rejected: cannot find your (reverse )?hostname\b)
^RCPT from [[3][]%(_port)s: 450 4.7.1 (<[^>]>)?: Helo command rejected: Host not found\b
^EHLO from [[4][]%(_port)s: 504 5.5.2 (<[^>]>)?: Helo command rejected: need fully-qualified hostname\b
^VRFY from [[5][]%(_port)s: 550 5.1.1\s
^RCPT from [[6][]%(_port)s: 450 4.1.8 (<[^>]>)?: Sender address rejected: Domain not found\b
^from [[7][]%(_port)s:?mdpr-auth = warning:
mdre-auth = ^[[8][]%(_port)s: SASL ((?i)LOGIN|PLAIN|(?:CRAM|DIGEST)-MD5) authentication failed:(?! Connection lost to authentication server| Invalid authentication mechanism)
mdre-auth2= ^[[9][]%(_port)s: SASL ((?i)LOGIN|PLAIN|(?:CRAM|DIGEST)-MD5) authentication failed:(?! Connection lost to authentication server)todo: check/remove “Invalid authentication mechanism” from ignore list, if gh-1243 will get finished (see gh-1297).
Mode “rbl” currently included in mode “normal”, but if needed for jail “postfix-rbl” only:
mdpr-rbl = %(mdpr-normal)s
mdre-rbl = ^RCPT from [[10]*[]%(_port)s: [45]54 [45].7.1 Service unavailable; Client host [\S+] blocked\bMode “rbl” currently included in mode “normal” (within 1st rule)
mdpr-more = %(mdpr-normal)s
mdre-more = %(mdre-normal)smdpr-ddos = lost connection after(?! DATA) [A-Z]+
mdre-ddos = ^from [[11]*[]%(_port)s:?mdpr-extra = (?:%(mdpr-auth)s|%(mdpr-normal)s)
mdre-extra = %(mdre-auth)s
%(mdre-normal)smdpr-aggressive = (?:%(mdpr-auth)s|%(mdpr-normal)s|%(mdpr-ddos)s)
mdre-aggressive = %(mdre-auth2)s
%(mdre-normal)sfailregex = <mdre->
Parameter “mode”: more (default combines normal and rbl), auth, normal, rbl, ddos, extra or aggressive (combines all)
Usage example (for jail.local):
[postfix]
mode = aggressive
# or another jail (rewrite filter parameters of jail):
[postfix-rbl]
filter = postfix[mode=rbl]
mode = more
ignoreregex =
[Init]
journalmatch = _SYSTEMD_UNIT=postfix.service
Author: Cyril Jaquier
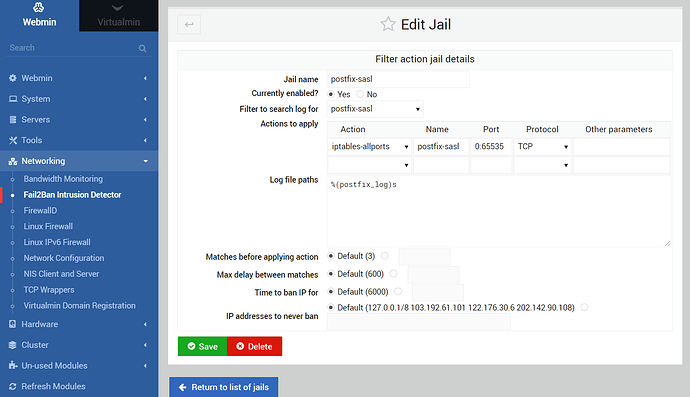
when i run: fail2ban-client status postfix-sasl
Status for the jail: postfix-sasl
|- Filter
| |- Currently failed: 7
| |- Total failed: 6454
| - File list: /var/log/mail.log - Actions
|- Currently banned: 16
|- Total banned: 54
`- Banned IP list: 212.70.149.55 212.70.149.71 77.40.3.8 78.128.113.131 87.246.7.226 …
but some ips always trying more than 3 and 10 and 1000 times…
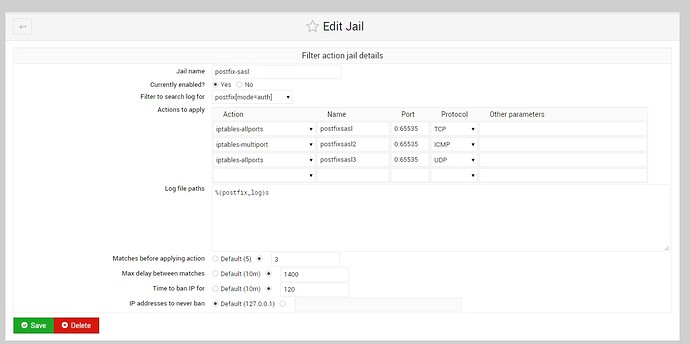
my config at jail:
are that commands iptables-all blocking - do i need something better like route/reject… at other-parameters need to type something ?
Yesterday i had 4GB logs of mail… ![]()
Thanks in advance…
Hope to find a solution… i have only 4 mail accounts and having problems… ![]()