thank you so much, it worked
don’t forget this has turned off the ability for any user to send emails
yes, this is exactly what i want
It doesn’t actually do that.
It prevents users from sending emails using Postfix. There are infinite other ways for users to send emails.
OP still needs to identify the root cause and address it.
It seems like the op has
I see no evidence they’ve identified the user(s) sending spam or the application doing so.
If they have an exploited web application (the most likely root cuase), spam is the least of their worries (but the spam will probably continue, as there are many ways to send spam aside from Postfix…if a web app is compromised, the attacker can use a variety of PHP libraries or shell scripts to send spam).
The op wanted to stop email being sent, that appears to have happened. The op may also have other issues but as of now the op is classing this as solved
Yeah, OP presented us with an XY problem. XY problem - Wikipedia
I’ve been trying to steer the conversation toward root cause, rather than symptom. OP has solved the symptom, not the root cause.
Who knows what the root cause was/is as the op didn’t give enough information on what problem needed to be solved
Yes, that’s true — I appreciate the clarification.
In the logs, I was seeing that someone was using my email address to send spam to Gmail and Yahoo addresses, and I couldn’t determine the exact cause. That’s why I wanted to stop outgoing email as a precaution.
Since then, I haven’t noticed any further suspicious activity, but like you’re saying, I still don’t know what the root cause was — whether it was a compromised web application, a user account, or something else. For now, blocking outgoing mail was just a quick way to stop the immediate problem until I can investigate further.
You have only stopped outgoing email from Postfix. There are many other ways an attacker can send email, if they’ve exploited a web application or user. If someone can run their own code on your server, they can send email.
I understand. I’ve changed all user passwords and stopped outgoing email from Postfix. Since then, I haven’t seen any suspicious activity. I’m not experienced enough to investigate further in depth, but for now, everything seems to be under control.
You not running a php website like wordpress that can send emails?
no, only have roundcube installed
So? you are running PHP ! on a webserver https://roundcube.net/about/
the door is open
So, what would you suggest I do in this case? How can I “close the door” while still keeping Roundcube installed and functional on the server
find out how you were compromised in the first place, this means reading through a pile of logs until you find the culprit, this is time consuming but is the only real way of finding out
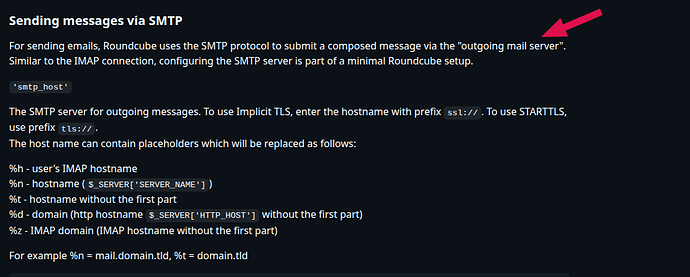
from roundcube’s documentation
the arrowed part of the document indicates that roundcube sends mail through postfix & not by another means, unless I read it wrong !
yes, but it remains a PHP app (although much of it is PERL based) which does mean it is open to just as many open doors as WordPress or any other PHP app.
but you are correct a deep dive and effort + time is needed to get to the bottom of this.
the point i was replying to was the apparent belief by the OP that a PHP webserver was not being used
Thanks for the clarification—and as I mentioned earlier, I’m still new to all this, so I really appreciate the insights and the heads-up.